Unveiling Vulnerabilities with CVEMap: Navigating the Cybersecurity Jungle
In the ever-evolving world of cybersecurity, the rise in reported Common Vulnerabilities and Exposures (CVEs) poses a significant challenge for security professionals. The sheer volume and occasionally exaggerated severity of these vulnerabilities can create a “noise” that distracts from critical security efforts. Enter CVEMap, a powerful and user-friendly tool designed by ProjectDiscovery to simplify the exploration of CVEs and enhance cybersecurity decision-making.
Understanding CVEMap
CVEMap is a command-line interface (CLI) tool developed to provide a structured and easily navigable way to explore CVEs. It addresses the challenges posed by the overwhelming number of vulnerabilities by consolidating data from various public sources, including the National Vulnerability Database (NVD), CISA’s Known Exploited Vulnerabilities Catalog (KEV), HackerOne’s CVE Discovery, and more.
Why CVEMap Matters for Cybersecurity Professionals
1. Multidimensional Prioritization
CVEMap transcends traditional vulnerability scoring systems. It adopts a multidimensional perspective, weighing factors like exploitability, critical due dates, and probabilistic assessments. This holistic approach ensures a comprehensive analysis, facilitating the effective prioritization of vulnerabilities.
2. Diverse Data Sources
Harnessing the power of sources such as KEV (Known Exploited Vulnerabilities), EPSS (Exploit Prediction Scoring System), Proofs of Concept (POCs), and HackerOne CVE Discovery, CVEMap paints a vivid picture of the threat landscape. By considering actively exploited vulnerabilities, exploit prediction scores, and bug bounty reports, it provides cybersecurity professionals with a nuanced understanding of potential threats.
3. User-Friendly Interface
CVEMap is purpose-built for practitioners and security engineers who prioritize genuine security measures over compliance checkboxes. Its structured format and customizable filters make it accessible for professionals at all levels. Navigating the tool is intuitive, enhancing the user experience for those deeply entrenched in the field.
Key Features of CVEMap
Mapping Capabilities:
CVE to EPSS, KEV, CPE, GitHub POCs, Nuclei Template, and HackerOne report mapping functionalities enhance the understanding of vulnerabilities.Customizable Filters:
Users can tailor their queries based on various criteria such as vendor, product, severity, and more, allowing for personalized and targeted exploration.User-Friendly Output:
The tool supports JSON output and provides a clean, structured output format. It enables users to choose the fields they want to display and exclude, making the information easily digestible.
Getting Started with CVEMap
Installation:
Installing CVEMap is straightforward. With Go 1.21 or later, users can run a simple command or download pre-compiled binaries from the release page.
go install github.com/projectdiscovery/cvemap/cmd/cvemap@latest
Configuration:
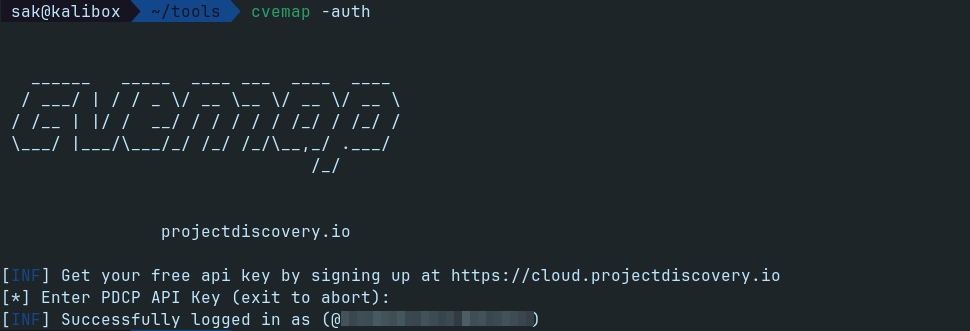
To use CVEMap, users need a ProjectDiscovery Cloud Platform (PDCP) account and API key. Configuration is simple and can be done using environment variables or an interactive authentication option.
cvemap -auth
Running CVEMap:
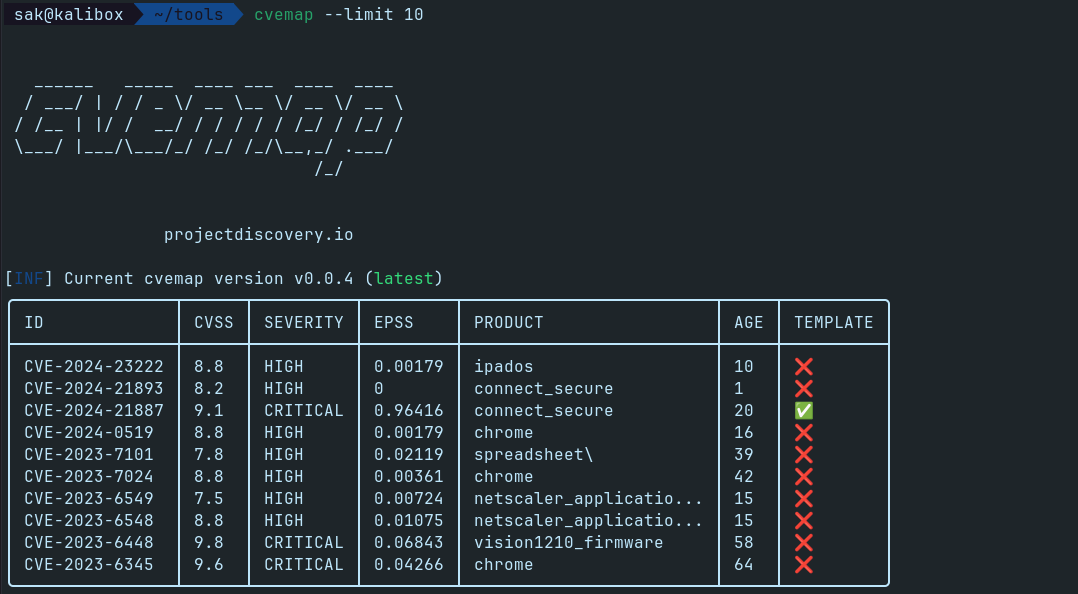
The tool provides various options for searching and filtering CVE data. Users can explore known exploited vulnerabilities, filter by severity, vendor, or product, and even display results in JSON format.
cvemap --limit 10
Usage Examples
Basic Usage
To get acquainted with CVEMap, run the following command to display the tool’s help information:
cvemap -h
Navigate the CVE jungle with ease.
Usage:
cvemap [flags]
Flags:
CONFIG:
-auth configure projectdiscovery cloud (pdcp) api key
OPTIONS:
-id string[] cve to list for given id
-cwe, -cwe-id string[] cve to list for given cwe id
-v, -vendor string[] cve to list for given vendor
-p, -product string[] cve to list for given product
-eproduct string[] cves to exclude based on products
-s, -severity string[] cve to list for given severity
-cs, -cvss-score string[] cve to list for given cvss score
-c, -cpe string cve to list for given cpe
-es, -epss-score string cve to list for given epss score
-ep, -epss-percentile string[] cve to list for given epss percentile
-age string cve to list published by given age in days
-a, -assignee string[] cve to list for given publisher assignee
-vs, -vstatus value cve to list for given vulnerability status in cli output. supported: modified, rejected, unknown, new, confirmed, unconfirmed
UPDATE:
-up, -update update cvemap to latest version
-duc, -disable-update-check disable automatic cvemap update check
FILTER:
-q, -search string search in cve data
-k, -kev display cves marked as exploitable vulnerabilities by cisa (default true)
-t, -template display cves that has public nuclei templates (default true)
-poc display cves that has public published poc (default true)
-h1, -hackerone display cves reported on hackerone (default true)
-re, -remote display remotely exploitable cves (AV:N & PR:N | PR:L) (default true)
OUTPUT:
-f, -field value fields to display in cli output. supported: product, vendor, vstatus, age, kev, template, poc, epss, cwe, assignee,
-fe, -exclude value fields to exclude from cli output. supported: product, vendor, vstatus, age, kev, template, poc, epss, cwe, assignee,
-lsi, -list-id list only the cve ids in the output
-l, -limit int limit the number of results to display (default 50)
-offset int offset the results to display
-j, -json return output in json format
-epk, -enable-page-keys enable page keys to navigate results
DEBUG:
-version Version
-silent Silent
-verbose Verbose
-debug DebugThis command provides an overview of all available switches and options.
Example: Finding Application CVEs
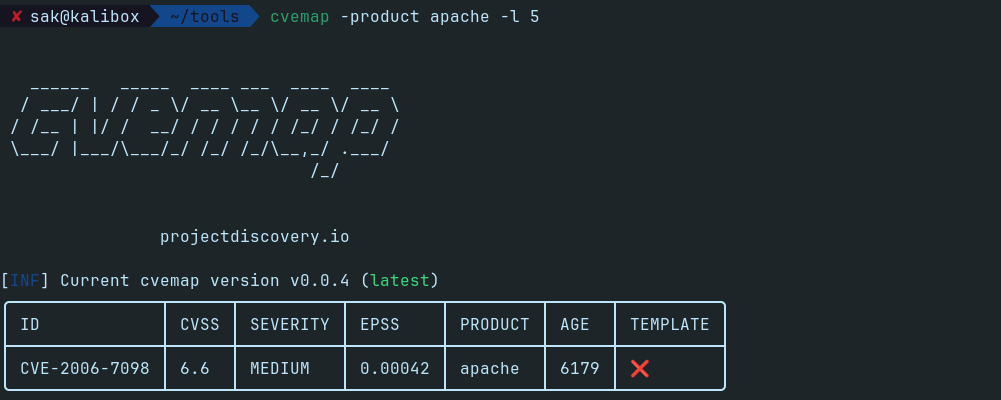
Imagine you’re responsible for the security of a web application, and you want to quickly identify any known vulnerabilities that might affect its components. Let’s use CVEMap to find CVEs associated with the popular web server software, Apache HTTP Server:
cvemap -product apache -l 5
To extract more detailed information about the identified CVEs, customize the output to display crucial information:
cvemap -product wordpress -field epss, product, severity, kev, age -l 5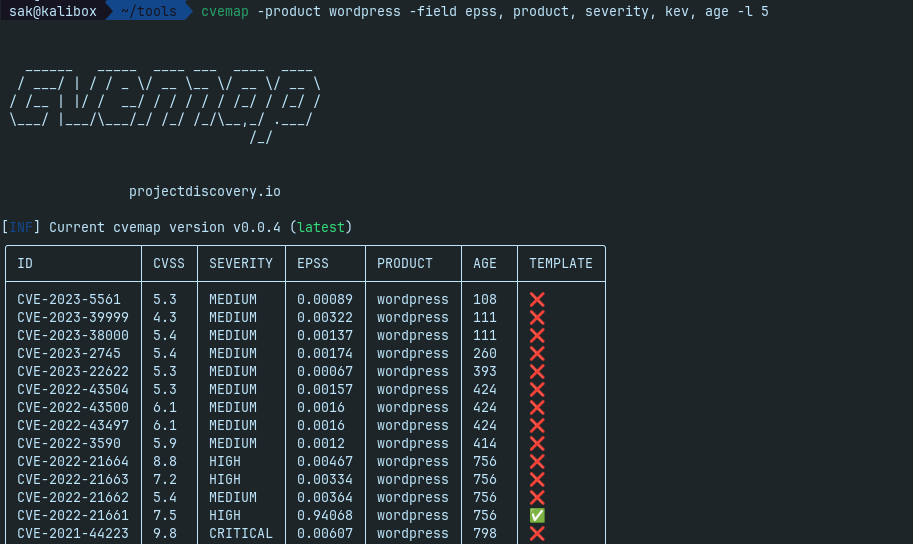
This example showcases the versatility of CVEMap in uncovering vulnerabilities specific to widely used web server software.
Conclusion
CVEMap from ProjectDiscovery is a game-changer in the cybersecurity space. For professionals, it offers advanced capabilities for prioritizing and understanding vulnerabilities, while its user-friendly interface makes it accessible for individuals looking to gain insights into the world of cybersecurity. Whether you’re a seasoned cybersecurity expert or someone curious about online threats, CVEMap provides a valuable tool for navigating the complex landscape of CVEs.
For more information and to get started, visit the CVEMap GitHub repository and explore the official documentation.
Remember, in the face of growing cyber threats, knowledge is the best defense. CVEMap empowers you to stay informed and take proactive measures in the ever-changing cybersecurity landscape. Stay secure, stay vigilant!

Comments