Docker Zero to Hero For Hackers: A Practical Guide for Cybersecurity Enthusiasts

Docker is an open-source platform designed to empower developers by facilitating the building, shipping, and running of applications within containers. As a lightweight and portable containerization technology, Docker wraps an application and its dependencies into a container, allowing easy deployment across diverse host systems. In this blog post, we’ll delve into the fundamental concepts of Docker, breaking down the intricacies for cybersecurity enthusiasts. We’ll cover container basics, Docker architecture, and provide practical examples of how Docker can be a game-changer in the realm of cybersecurity.
What is a container?
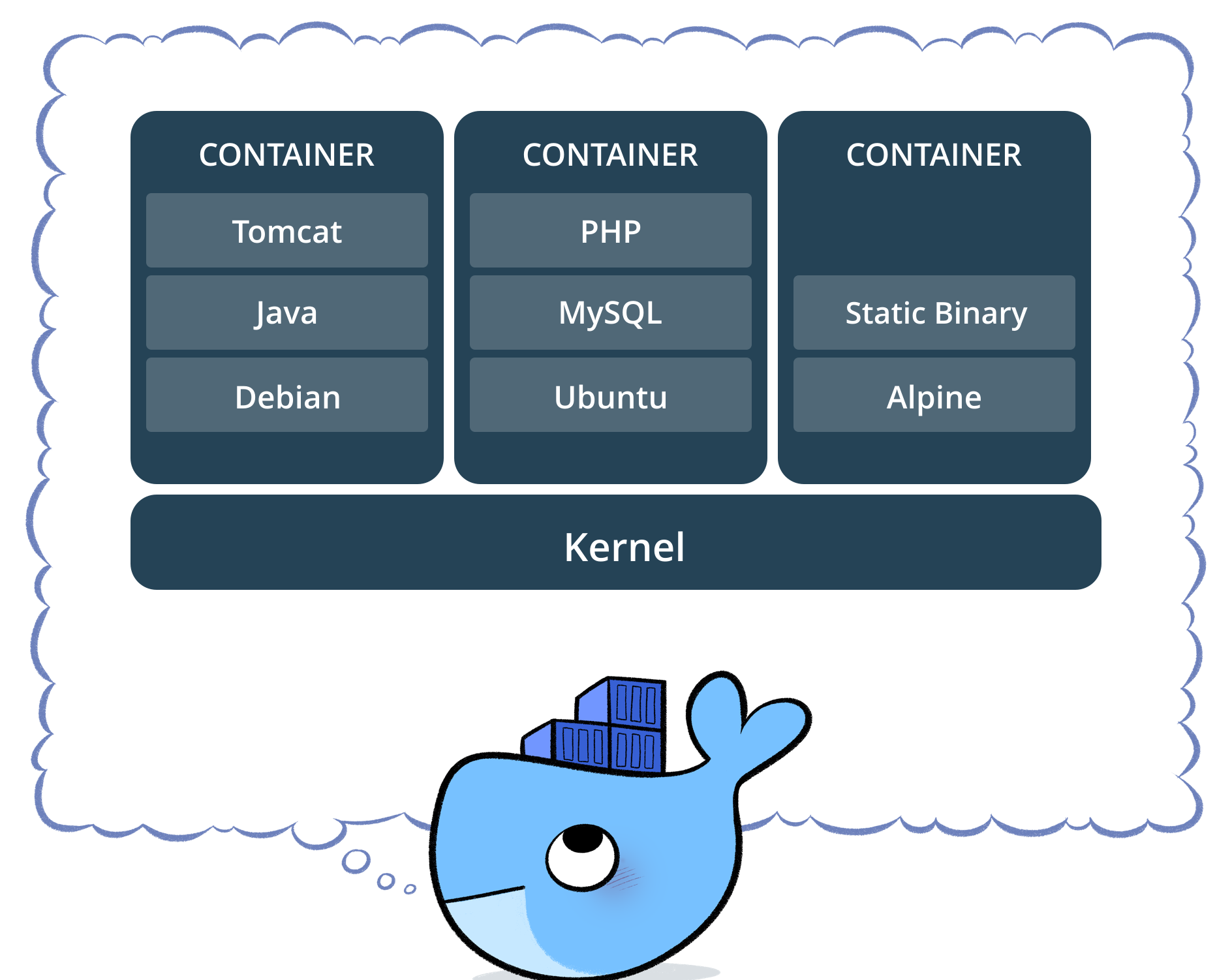
A container is a standardized unit of software bundling code and its dependencies. It ensures swift and reliable application execution across different computing environments. In cybersecurity terms, a container serves as a secure vault encapsulating an application, its libraries, and essential system dependencies. The lightweight and portable nature of containers makes them ideal for cybersecurity tasks, enabling seamless deployment in various environments.
Containers vs Virtual Machines
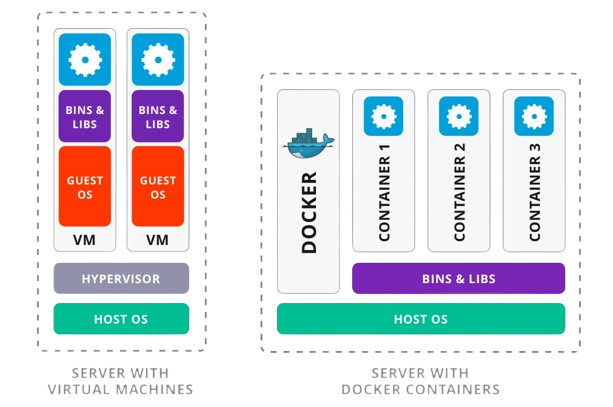
Containers and virtual machines (VMs) both isolate applications and their dependencies, yet they differ significantly:
Resource Utilization: Containers share the host OS kernel, making them lighter and faster compared to VMs, which require a full-fledged OS.
Portability: Containers excel in portability, capable of running on any system with a compatible host OS. VMs, however, rely on specific hypervisors for compatibility.
Security: VMs offer heightened security with isolated operating systems. Containers, sharing the host OS, provide less isolation but are more manageable.
Management: Container management is generally easier due to their lightweight and agile nature.
Why are containers lightweight?
Containers achieve their lightweight nature through containerization, a technology enabling them to share the host OS kernel and libraries while maintaining application isolation. This results in a compact footprint compared to traditional virtual machines, as containers exclude a full OS, further minimizing their size.
Docker Architecture
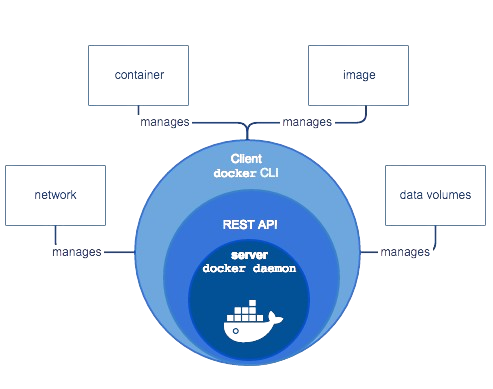
Docker follows a client-server architecture comprising:
Docker Client: A command-line interface (CLI) tool sending commands to the Docker daemon.
Docker Daemon: The server component managing Docker objects such as images, containers, networks, and volumes.
Docker Registry: A central repository storing Docker images.
The Docker lifecycle involves creating a Dockerfile, building a Docker image, running a Docker container, and pushing the Docker image to a registry. Here’s a brief overview:
- Create a Dockerfile: A text file with instructions for building a Docker image.
- Build the Docker image: Use the Dockerfile to create a read-only template.
- Run the Docker container: Create a running instance of the image.
- Push the Docker image: Share the built image on a Docker registry for collaboration.
Docker LifeCycle
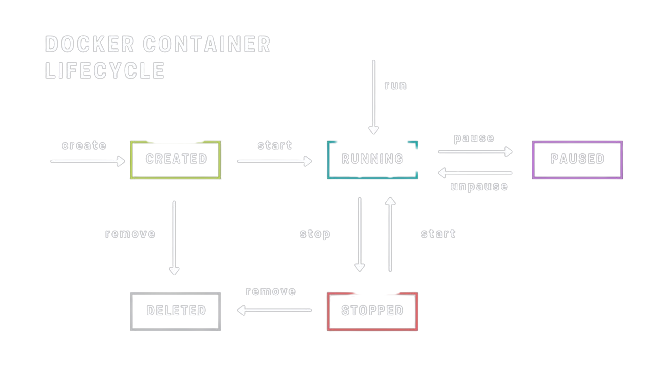
docker build: Builds Docker images from a Dockerfile.docker run: Runs a container from Docker images.docker push: Pushes the container image to public/private registries for sharing.
Understanding the Terminology
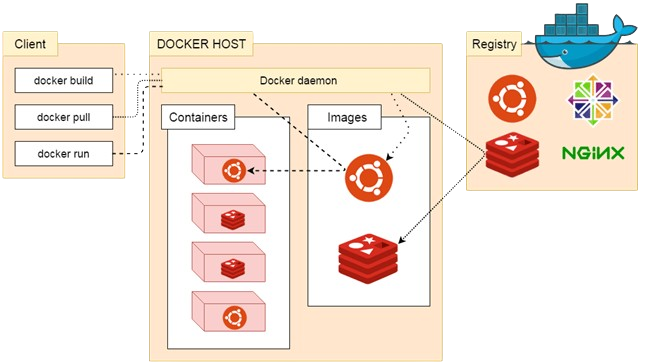
Docker Daemon
The Docker daemon listens for Docker API requests, managing Docker objects like images, containers, networks, and volumes. Daemons can communicate with each other to handle Docker services.
Docker Client
The Docker client is the primary way users interact with Docker. Commands such as docker run are sent to the client, which executes them. The Docker client can communicate with multiple daemons.
Docker Desktop
Docker Desktop is an easy-to-install application for Mac, Windows, or Linux environments. It includes the Docker daemon, Docker client, Docker Compose, Docker Content Trust, Kubernetes, and Credential Helper.
Docker Registries
Docker registries store Docker images. Docker Hub is a public registry, and Docker is configured to look for images there by default. Users can also run private registries.
INSTALL DOCKER

For detailed instructions on installing Docker, visit Docker Installation Guide.
For a quick demo, create an Ubuntu EC2 instance on AWS and execute the following commands:
sudo apt update
sudo apt install docker.io -y
Start Docker and Grant Access
After installing Docker, ensure the Docker daemon is running. Verify with:
sudo systemctl status docker
If not running, start the daemon:
sudo systemctl start docker
Grant access to your user:
sudo usermod -aG docker ubuntu
Log out and log back in for changes to take effect.
Verify Docker installation:
docker run hello-world
Docker is Installed, up and running
Use the same command to confirm:
docker run hello-world
Docker Images for Cybersecurity/Pentesting
Docker provides a rich ecosystem of pre-built images tailored for cybersecurity and penetration testing, offering versatility and efficiency in setting up security environments. Here are additional examples of Docker images that cater to specific cybersecurity needs:
Kali Linux
Kali Linux is a widely-used Linux distribution for penetration testing, forensics, and security auditing. The Kali Linux Docker image is a versatile tool for cybersecurity practitioners. It includes a plethora of tools such as Wireshark, Nmap, Burp Suite, and John the Ripper.
docker pull kalilinux/kali-linux-dockerExample Usage:
docker run -it kalilinux/kali-linux-docker /bin/bashAdditional Example 1: Launching Wireshark for network analysis within the Kali Linux container:
docker run -it --rm --net=host --cap-add=NET_ADMIN kalilinux/kali-linux-docker wiresharkIn this scenario, the container gains access to the host network stack, enabling network analysis with Wireshark directly from the container.
Additional Example 2: Performing a quick Nmap scan on a target:
docker run -it --rm kalilinux/kali-linux-docker nmap -p 1-1000 192.168.1.1This command runs an Nmap scan against the specified IP address, showcasing the utility of Kali Linux tools within the Docker container.
Additional Example 3: Using John the Ripper to crack passwords:
docker run -it --rm kalilinux/kali-linux-docker john --wordlist=/usr/share/wordlists/rockyou.txt /path/to/password/fileHere, the container employs John the Ripper to attempt password cracking using a common wordlist.
Metasploit Framework
Metasploit Framework is a powerful open-source tool for penetration testing, vulnerability research, and development. The Metasploit Framework Docker image simplifies the setup of Metasploit within a controlled environment.
docker pull metasploitframework/metasploit-frameworkExample Usage:
docker run --rm -it metasploitframework/metasploit-frameworkAdditional Example 1: Running an auxiliary module for HTTP enumeration:
docker run --rm -it metasploitframework/metasploit-framework msfconsole -x "use auxiliary/scanner/http/http_enum; set RHOSTS 192.168.1.1; run"This command launches Metasploit and executes an HTTP enumeration scan against the specified target.
Additional Example 2: Exploiting a known vulnerability using Metasploit:
docker run --rm -it metasploitframework/metasploit-framework msfconsole -x "use exploit/windows/smb/ms08_067_netapi; set RHOSTS 192.168.1.1; run"Here, Metasploit is utilized to exploit a specific Windows SMB vulnerability on the given IP address.
Additional Example 3: Brute-forcing SSH credentials using Metasploit:
docker run --rm -it metasploitframework/metasploit-framework msfconsole -x "use auxiliary/scanner/ssh/ssh_login; set RHOSTS 192.168.1.1; set USER_FILE /path/to/usernames.txt; set PASS_FILE /path/to/passwords.txt; run"This command demonstrates using Metasploit for SSH credential brute-forcing.
Conclusion
Docker has revolutionized software development and deployment. Its ability to package applications and dependencies into portable containers streamlines deployment across different environments. Docker’s versatility and user-friendly approach make it an ideal solution for modern software development practices, including continuous integration and delivery. Embrace Docker, and let your journey from zero to hero in the cybersecurity landscape begin!

Comments