Hackviser - Basic Command Injection Writeup

Basic Command Injection -
This lab exposes a Command Injection vulnerability, allowing for remote command execution.
The web application takes the desired domain name as a parameter for the “nslookup” utility in the terminal. Your task is to execute a command on the system.
What’s the hostname address of the server hosting the website?
What is OS Command Injection?
OS Command Injection represents a vulnerability wherein attackers can run arbitrary commands on the underlying operating system by manipulating user-provided input passed to system shell commands. This vulnerability emerges when web applications directly integrate user input into command strings sans adequate validation or sanitization.
Impact of OS Command Injection
OS Command Injection can result in severe consequences, including unauthorized access, data theft, or complete control over the target system. Attackers exploit this vulnerability to execute commands using the vulnerable application’s privileges, posing significant threats to system security and integrity.
Read more: Exploring OS Command Injection: Understanding and Hands-On Practice
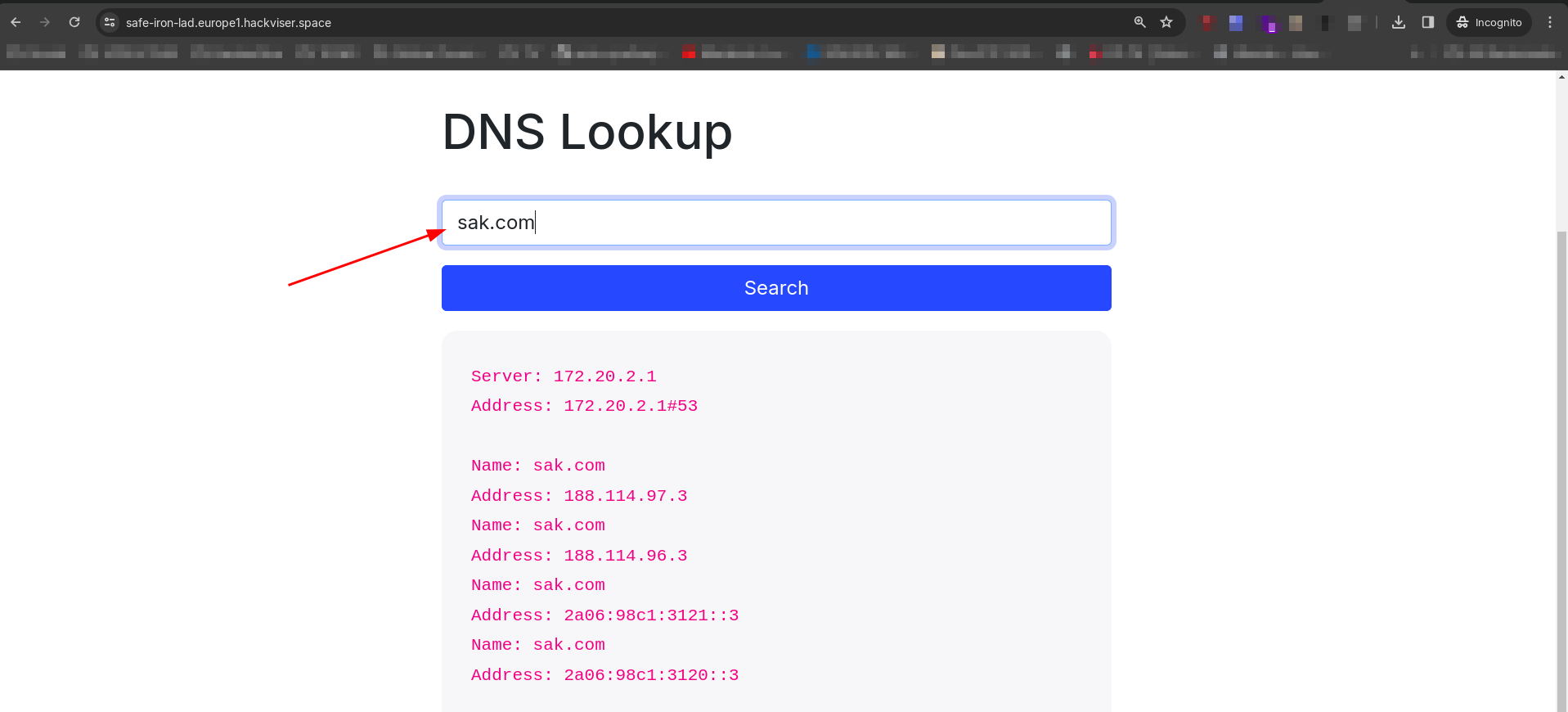
In this challenge, we’re given a parameter where we can input a URL for scanning. Behind the scenes, it utilizes nslookup to gather information about the entered domain.
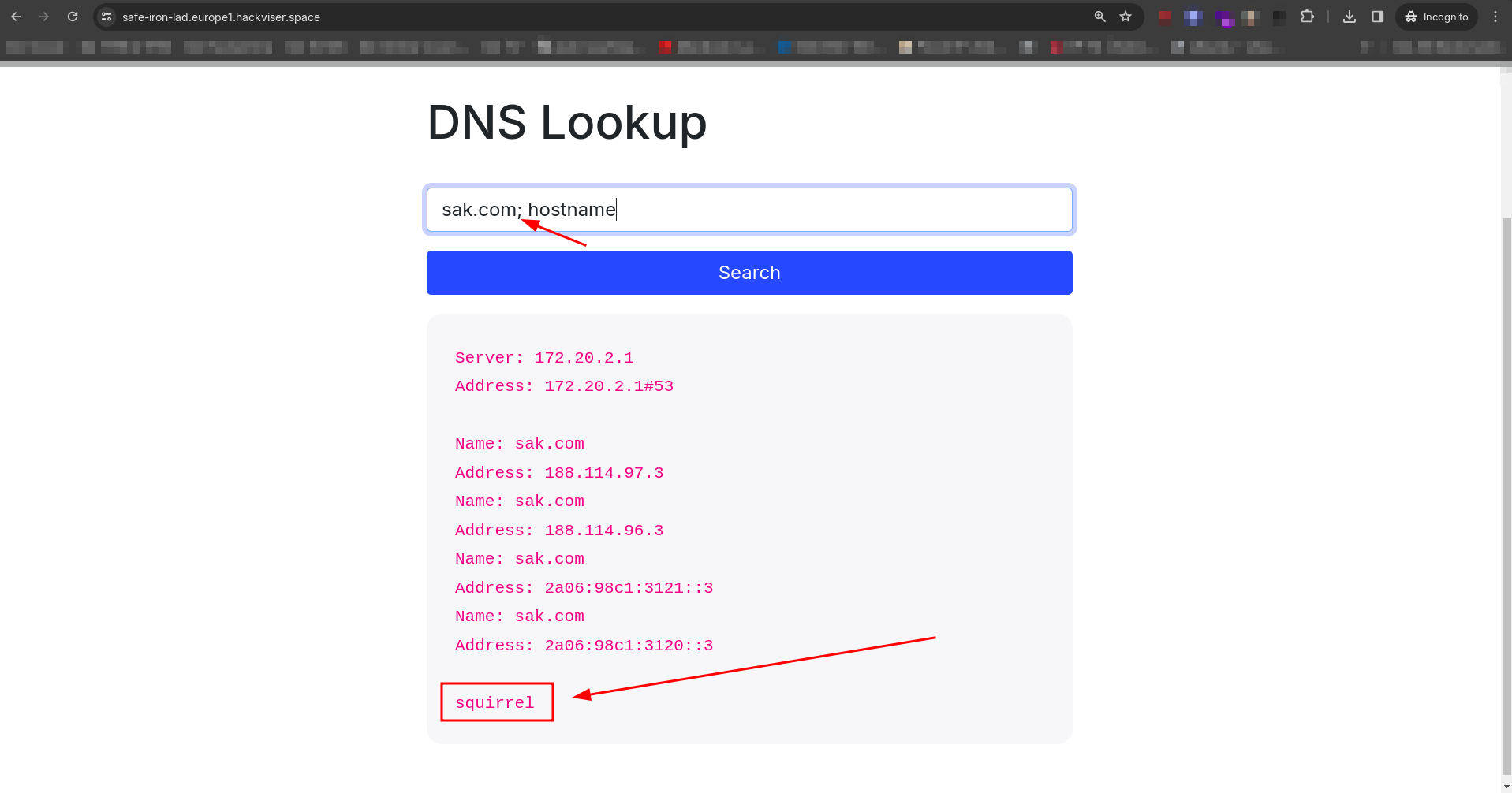
To execute command injection, I simply used a semicolon to append a Linux command alongside the input URL. In this challenge, we need to discover the hostname of the server. Therefore, my payload was:
sak.com; hostnameThe payload succeeded, yielding the hostname “squirrel.”
Conclusion:
Command Injection vulnerabilities, such as the one demonstrated in this lab, underscore the critical importance of input validation and sanitization in web application development. Failure to properly handle user input can open the door to malicious exploitation, potentially leading to serious security breaches and compromise of sensitive systems. It’s imperative for developers to implement robust security measures, including input validation and segregation of commands, to mitigate the risks associated with Command Injection attacks.

Comments