Cybersecurity Playground: Installing OWASP Juice Shop on Ubuntu with Docker – A Step-by-Step Guide

In the realm of cybersecurity education and training, practical hands-on experience is invaluable. Recognizing this need, OWASP (Open Web Application Security Project) introduced the Juice Shop – an intentionally vulnerable web application designed to simulate real-world security challenges. This blog post aims to provide a detailed walkthrough on installing OWASP Juice Shop on Ubuntu using Docker, allowing enthusiasts and professionals alike to delve into the intricacies of web security in a controlled environment.
What is OWASP Juice Shop?

The OWASP Juice Shop is not your typical online store; it serves as a playground for security enthusiasts and professionals to hone their skills in identifying and exploiting web application vulnerabilities. Concealed beneath its facade as a fruit and vegetable juice shop lie 102 deliberately planted challenges of varying difficulty levels, representing common security vulnerabilities encountered in modern web development.
The Juice Shop’s development commenced in September 2014, driven by the necessity for a contemporary security training environment that reflects the intricacies of current web technologies. Over the years, it has evolved into a sophisticated platform, leveraging modern frameworks such as Angular, JavaScript, Node.js, and SQLite for its database.
Vulnerability Categories:
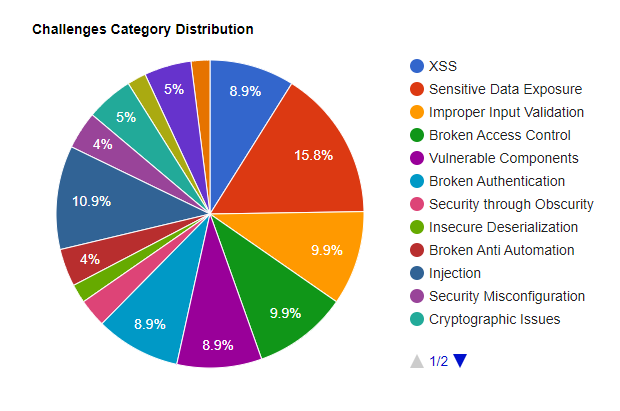
In OWASP Juice Shop, vulnerabilities are meticulously categorized into various classes, covering a wide spectrum of risk and vulnerability types identified in well-known lists and documents such as OWASP Top 10, OWASP ASVS, OWASP Automated Threat Handbook, OWASP API Security Top 10, OWASP Top 10 Privacy Risks, and MITRE’s Common Weakness Enumeration (CWE). This structured approach enables users to target specific areas of interest and gain comprehensive insights into web application security.
- Category Breakdown:
Category Mappings:
| Category | OWASP | CWE | WASC |
|---|---|---|---|
| Broken Access Control | A1:2021, API1:2019, API5:2019 | CWE-22, CWE-285, CWE-639, CWE-918 | WASC-02, WASC-09, WASC-16 |
| Broken Anti-Automation | OWASP-AT-004, API4:2019, OWASP-AT-010, … | CWE-362 | WASC-11, WASC-21 |
| Broken Authentication | A7:2021, API2:2019, P6:2021 | CWE-287, CWE-352 | WASC-01, WASC-49 |
| Cross Site Scripting (XSS) | A3:2021, A7:2017 | CWE-79 | WASC-8 |
| Cryptographic Issues | A2:2021 | CWE-326, CWE-327, CWE-328, CWE-950 | - |
| Improper Input Validation | ASVS V5, API6:2019 | CWE-20 | WASC-20 |
| Injection | A3:2021, API8:2019, P1:2021 | CWE-74, CWE-89 | WASC-19, WASC-28, WASC-31 |
| Insecure Deserialization | A8:2021, A8:2017 | CWE-502 | - |
| Miscellaneous | P5:2021 | - | - |
| Security Misconfiguration | A5:2021, A9:2021, API7:2019, API9:2019, … | CWE-209 | WASC-14, WASC-15 |
| Security through Obscurity | A4:2021, P5:2021 | CWE-656 | - |
| Sensitive Data Exposure | A3:2017, API3:2019, OTG-CONFIG-004, P2:2021 | CWE-200, CWE-530, CWE-548 | WASC-13 |
| Unvalidated Redirects | A10:2013 | CWE-601 | WASC-38 |
| Vulnerable Components | A6:2021 | CWE-829, CWE-506, CWE-1104 | - |
| XML External Entities (XXE) | A5:2021, A4:2017 | CWE-611 | WASC-43 |
Each category represents a distinct aspect of web application security, ranging from access control and authentication to cryptographic issues and injection vulnerabilities. By aligning Juice Shop’s challenges with these standardized categories, users can effectively address specific security concerns and enhance their understanding of prevalent threats in the digital landscape.
Installing OWASP Juice Shop on Ubuntu with Docker:
Now, let’s dive into the installation process of OWASP Juice Shop on Ubuntu using Docker. While the initial instructions provided focused on Kali Linux, the procedure remains largely similar for Ubuntu.
Begin by updating the package index and installing Docker using the following commands:
sudo apt update sudo apt install -y docker.ioAfter installation, start the Docker service and enable it to launch automatically upon system reboot:
sudo systemctl enable docker --nowTo grant your user permission to use Docker, add it to the docker group:
sudo usermod -aG docker $USERReload the group settings for the changes to take effect:
newgrp dockerWith Docker installed, pulling and running OWASP Juice Shop is a breeze. Execute the following command to download and launch the Juice Shop container:
docker run --rm -p 3000:3000 bkimminich/juice-shopIf necessary, pull the Juice Shop image first using:
docker pull bkimminich/juice-shopOnce the container is running, access OWASP Juice Shop via http://localhost:3000/ in your web browser.
Conclusion:
In conclusion, OWASP Juice Shop stands as a testament to the commitment towards enhancing web application security through hands-on learning and gamification. By leveraging Docker, enthusiasts and professionals can swiftly set up and explore the intricacies of web security in a controlled environment. Embrace the challenges, uncover vulnerabilities, and embark on a journey towards mastering the art of cybersecurity with OWASP Juice Shop.

Comments