denied - A Web Challenge Walkthrough from AmateursCTF 2024
The AmateursCTF 2024 had a tricky web puzzle called "denied." They gave us a file named index.js for this challenge. When we went to the website, all we saw was a message saying Bad! Nothing else, even when we peeked at the code behind the page.
Let's checked out the index.js file to see what it was hiding:
index.js:
const express = require('express')
const app = express()
const port = 3000
app.get('/', (req, res) => {
if (req.method == "GET") return res.send("Bad!");
res.cookie('flag', process.env.FLAG ?? "flag{fake_flag}")
res.send('Winner!')
})
app.listen(port, () => {
console.log(`Example app listening on port ${port}`)
})This code sets up a basic Express.js server. It listens on port 3000. When you visit the root URL ("/") with a GET request, it checks if the request method is GET; if it is, it sends "Bad!" as the response. Otherwise, it sets a cookie named 'flag' with the value from the environment variable process.env.FLAG, or if that's not set, it uses "flag{fake_flag}". Finally, it sends "Winner!" as the response.
We decided to use a tool called BurpSuite to help us out. We intercepted and replayed requests using BurpSuite's Repeater, trying different methods.
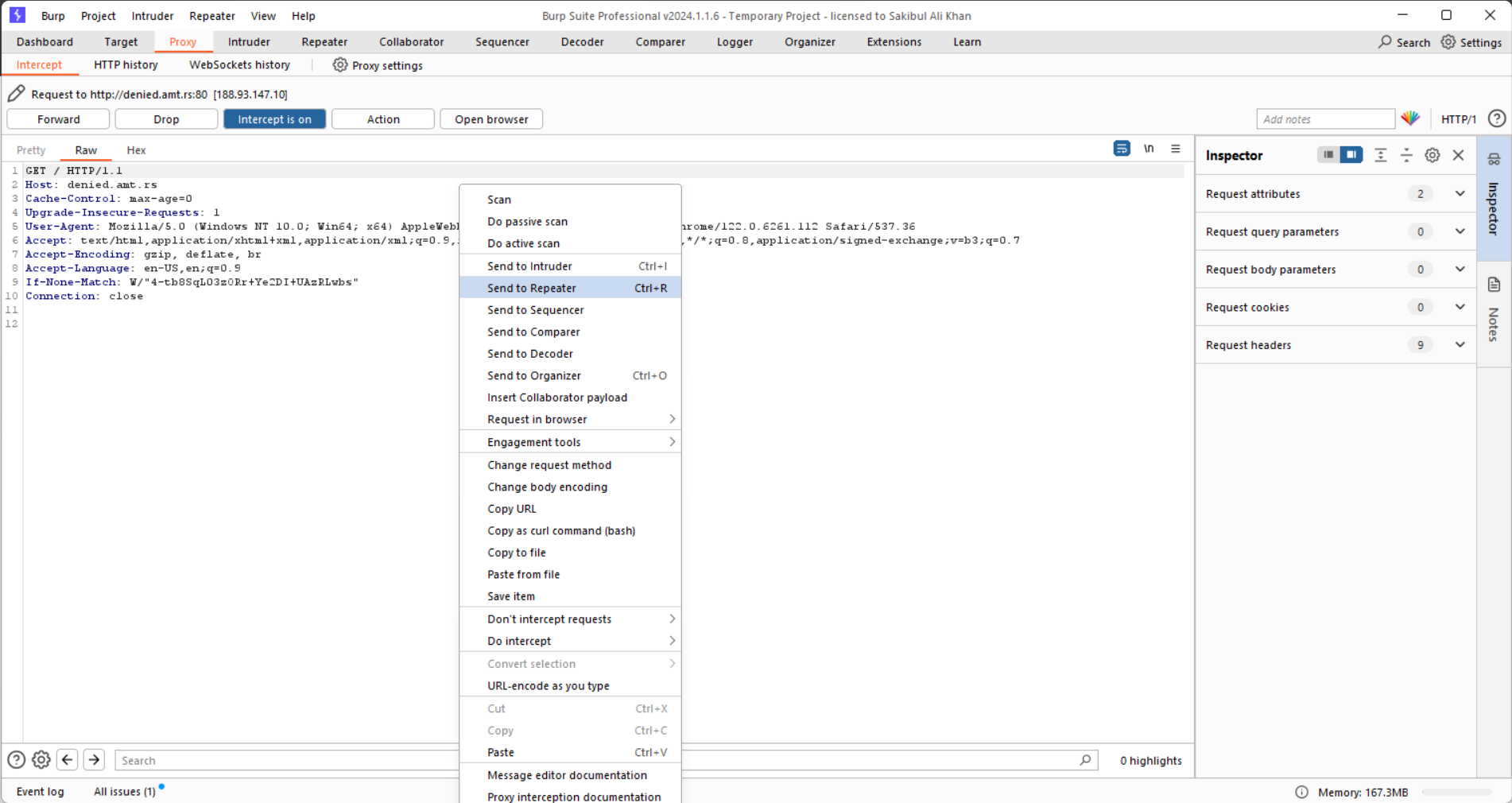
After a few tries, we found out that only GET and HEAD methods worked, as shown by an OPTIONS request.
We went with the HEAD method and, lo and behold, we found a hidden, URL-encoded flag!
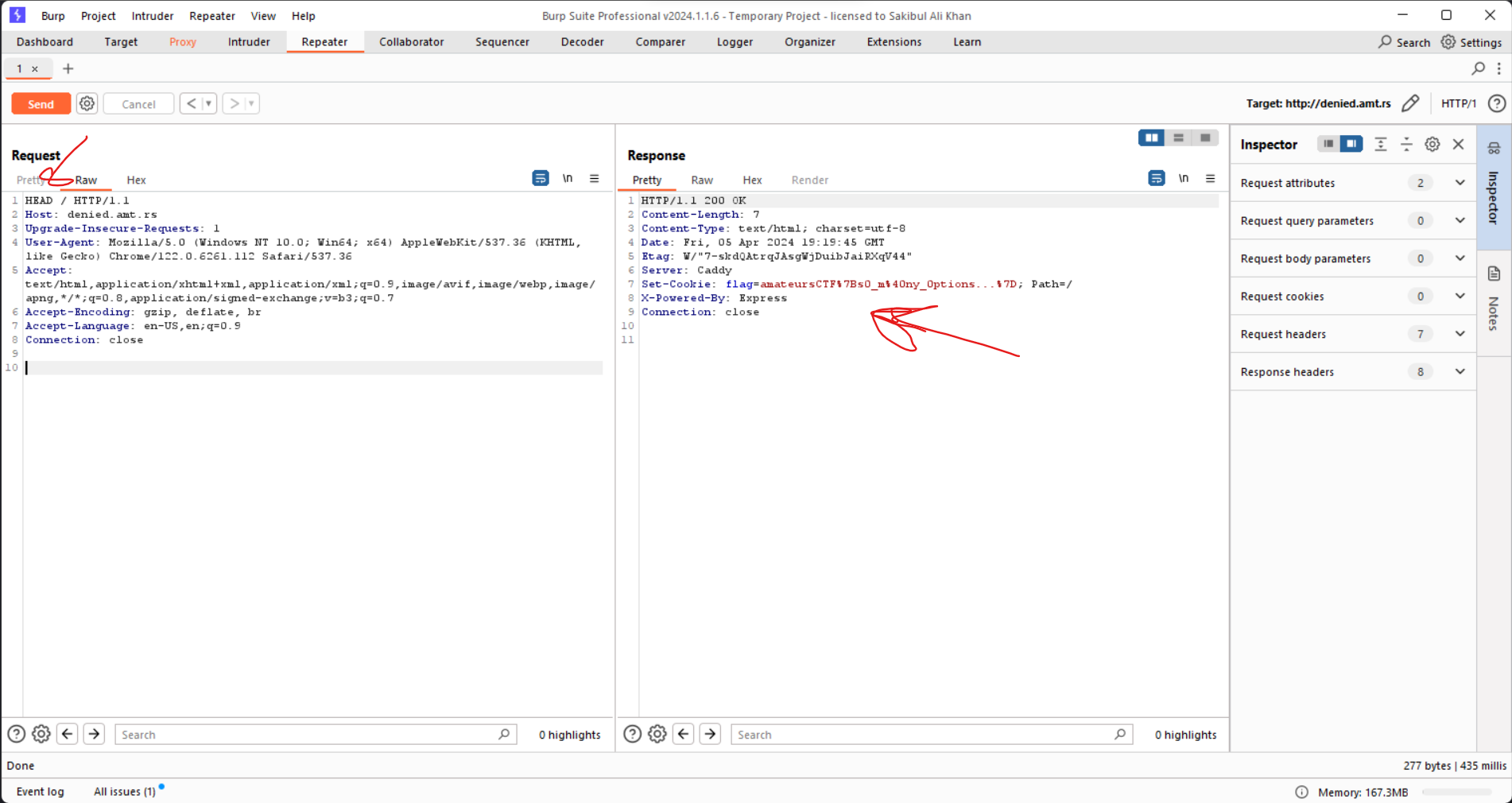
To decode the flag, we used BurpSuite's Decoder feature and selected "Decode as URL" from the menu.
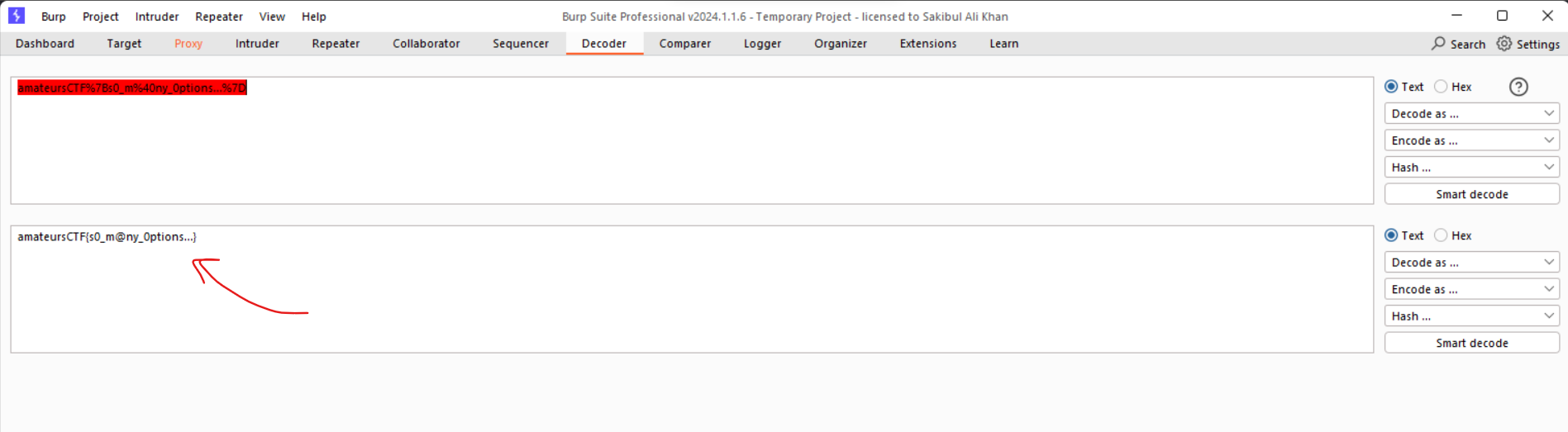
And there it was, the secret CTF challenge flag, decoded and ready for victory!
In the end, cracking the "Denied" challenge at AmateursCTF 2024 taught us the importance of not giving up and using our brains. By playing around with different methods and tools like BurpSuite, we were able to solve the puzzle and win. This challenge showed us that persistence and thinking outside the box are key in the world of cybersecurity puzzles.

Comments